A teenager responsible for a massive bitcoin scam last year that involved hacking Twitter accounts for various politicians and other high-profile figures has been sentenced to three years in prison.
A quarter (25%) of the surveyed UK workers said they allow their children to use their corporate device for home-schooling and other purposes, according to a YouGov survey conducted by iomart.
The UK government has set up a new independent body, the UK Cyber Security Council, to boost career opportunities and professional standards for the UK’s booming cyber security sector.
Microsoft has published a preliminary root cause analysis of its March 15 Azure Active Directory outage, which took down Office, Teams, Dynamics 365, Xbox Live, and other apps.
At least 23 telecommunications providers in Southeast Asia, Europe, and the United States, are suspected to have been targeted as part of the campaign that has been active since at least August 2020.
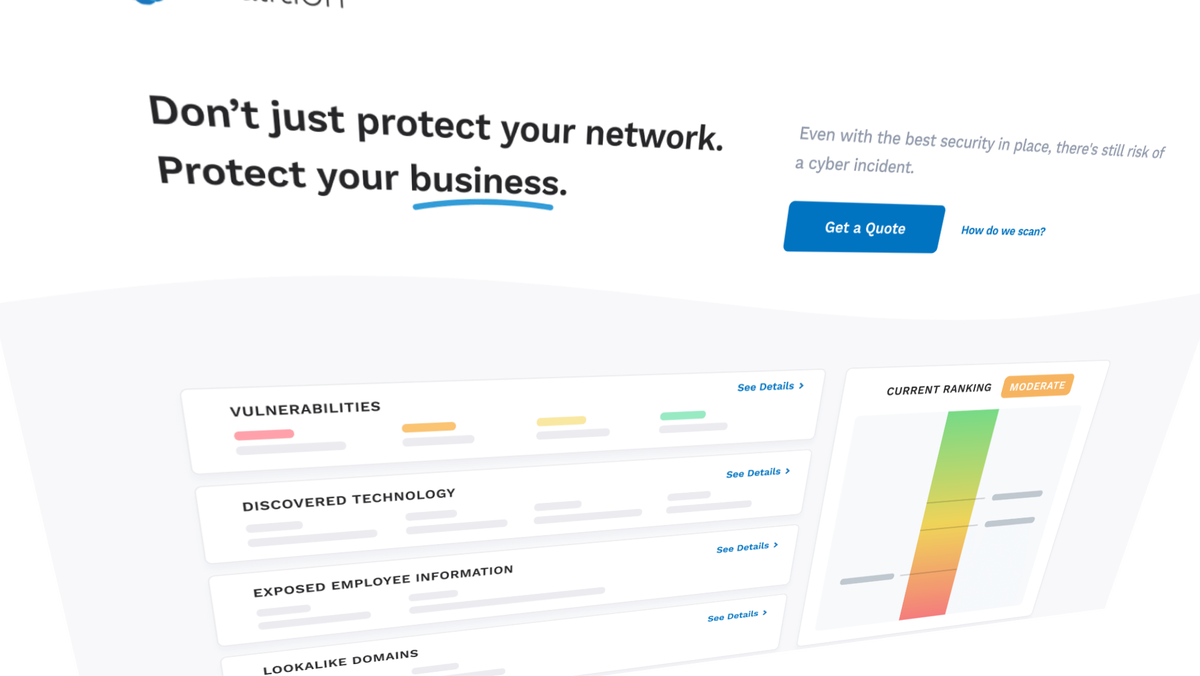
Coalition, an enterprise-grade cybersecurity platform that specializes in providing insurance, has raised $175 million in its Series D round of funding led by Index Ventures.
Dutch authorities on Tuesday said that the fallout for the Netherlands from a hack on Microsoft Corp’s Exchange was substantial, with at least 1,200 Dutch servers likely to have been affected.
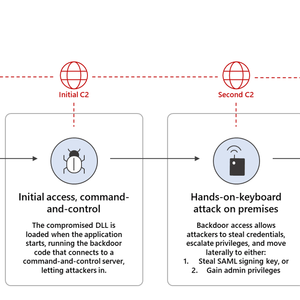
While hackers stole of its some source code, Mimecast added that the source code accessed by the hackers was incomplete and could not be used to build and run any component of the Mimecast service.
Plans from the Biden administration to release product security rating system could raise the bar for security overall, say experts, but won’t likely prevent the next SolarWinds or Microsoft hacks.
Secret information belonging to the UK Ministry of Defence was exposed to hostile states when it was transferred from secure networks to personal email accounts, Sky News has learnt.