Cloud security provider Wiz found two critical architecture flaws in generative AI models uploaded to Hugging Face, namely shared Inference infrastructure takeover and shared CI/CD takeover.
“An increase of attacks can currently be assumed, particularly in light of the upcoming European elections. These may include phishing attacks to publish stolen data or documents,” a BSI spokesperson told Information Security Media Group.
Cybersecurity researchers at Netenrich have uncovered a new ransomware group called Red Ransomware Group (Red CryptoApp). This group operates differently from typical ransomware outfits, adding a twist to their extortion tactics.
Newly discovered HTTP/2 protocol vulnerabilities called “CONTINUATION Flood” can lead to denial of service (DoS) attacks, crashing web servers with a single TCP connection in some implementations.
Vietnamese financially motivated hackers are targeting businesses across Asia in a campaign to harvest corporate credentials and financial data for resale in online criminal markets.
While similar to IcedID, Proofpoint researchers confirmed it is an entirely new malware, likely created by the IcedID developers. Latrodectus shares infrastructure overlap with historic IcedID operations.
First encountered in December 2019, JsOutProx is a RAT and highly obfuscated JavaScript backdoor that allows its operators to run shell commands, download additional payloads, execute files, capture screenshots, establish persistence, and more.
A very recent malvertising campaign was found impersonating the popular VPN software NordVPN. A malicious advertiser is capturing traffic from Bing searches and redirecting users to a decoy site that looks almost identical to the real one.
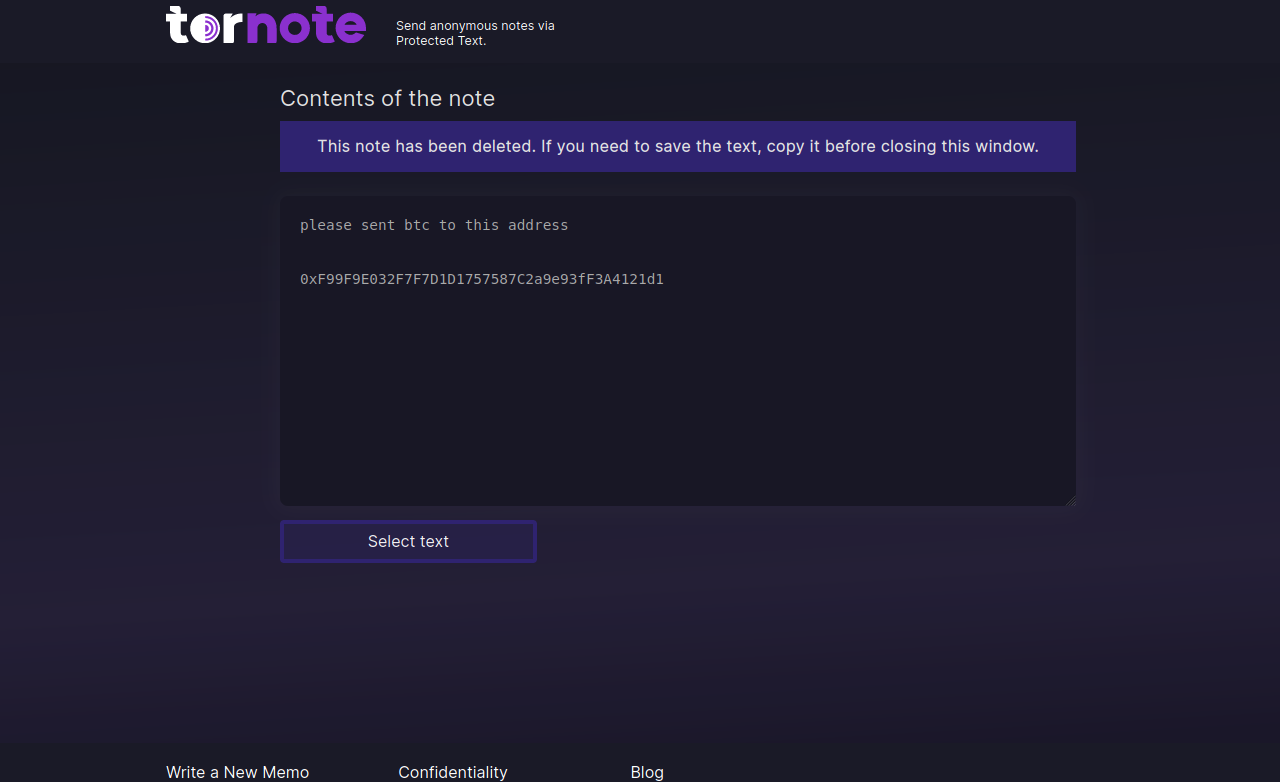
A cybercrook who has been setting up websites that mimic the self-destructing message service privnote.com accidentally exposed the breadth of their operations recently when they threatened to sue a software company.
In January 2024, FortiGuard Labs collected a PDF file written in Portuguese that distributes a multi-functional malware known as Byakugan. While investigating this campaign, a report about it was published.