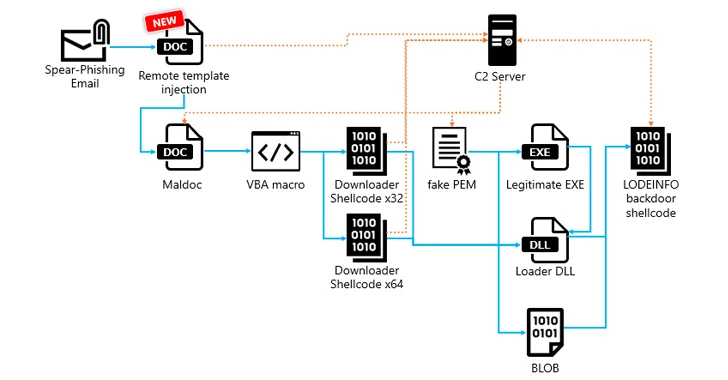
The malware has evolved with new features and anti-analysis techniques. It is linked to a Chinese nation-state actor known as Stone Panda and has been used in attacks targeting Japanese political establishments.
The study by a cybercrime researcher at the University of Twente analyzed ransomware attacks in the Netherlands from 2019-2022, finding that companies working with incident response firms were most likely to pay ransoms.
Members have expressed concern over potential data compromise and lack of communication from CAMC about the nature of the problem, leading to speculation about a ransomware-related security breach.
A new iOS 17 update brings Stolen Device Protection feature to prevent unauthorized access and actions on stolen iPhones. Thieves will have limited access to sensitive information and actions, requiring additional authentication for critical changes.
According to Trustpair, 96% of U.S. companies experienced at least one payment fraud attempt in the past year, with a 71% increase from the prior year, indicating a significant rise in fraudulent activities.
The performance goals consist of essential and enhanced practices based on industry cybersecurity frameworks and aim to address common vulnerabilities and mature cybersecurity capabilities in the healthcare sector.
A Netherlands-based medical laboratory’s unsecured database exposed 1.3 million records, including COVID test results and personal identifiable information, due to a configuration issue and lack of response to responsible disclosure notices.
In 2023, ReversingLabs identified a significant increase in malicious packages across open-source software platforms like npm, PyPI, and RubyGems. The number of malicious packages detected increased by 1,300% from 2020 and 28% from 2022.
The vulnerability, CVE-2024-23897, allows attackers to read arbitrary files on the Jenkins controller file system. This could potentially lead to various attacks, including remote code execution and decryption of stored secrets.
Apple’s lawsuit alleges that NSO Group facilitated hacking into Apple’s servers, leading to significant time and expense for Apple in detecting and eradicating Pegasus from users’ devices.