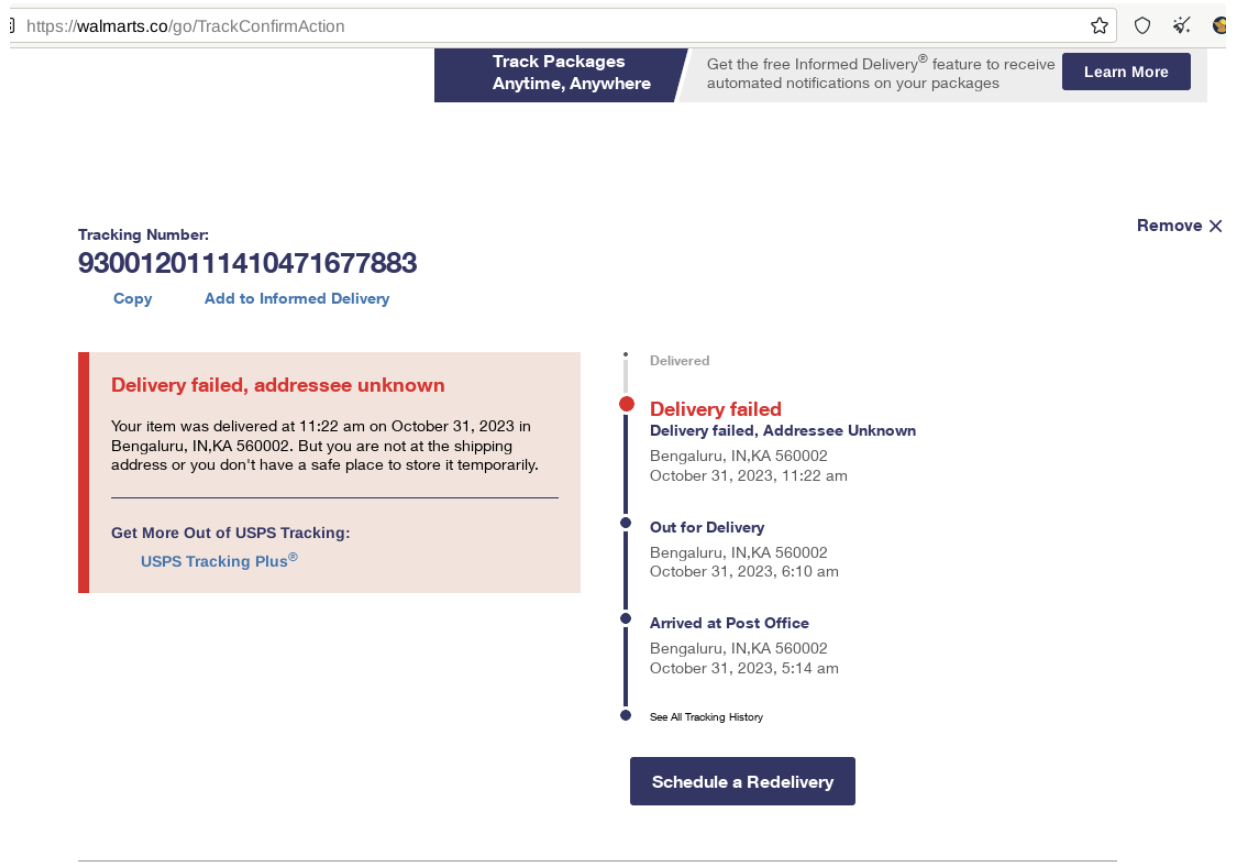
A new phishing campaign has been discovered that targets individuals with messages about failed deliveries or late payments from major shipping companies. It also involves the use of fake websites that mimic popular brands and postal services.
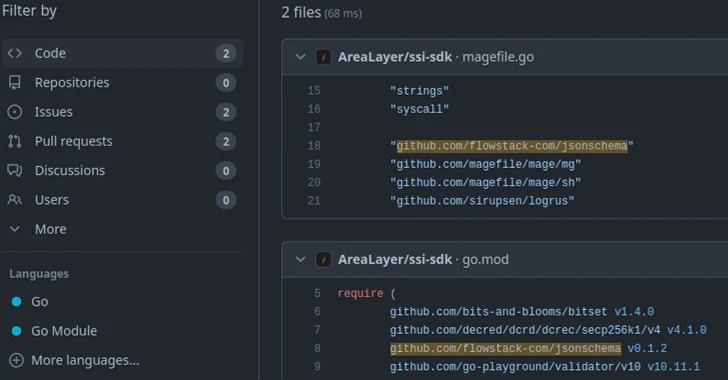
Go modules are particularly susceptible to repojacking due to their decentralized nature, and popular repository namespace retirement countermeasures are not effective in preventing all instances of this attack.
The St. Johns River Water Management District in Florida has confirmed that it responded to a cyberattack last week, amid warnings from top cybersecurity agencies about foreign attacks on water utilities.
A hacker group allegedly linked to Iran, known as Malek Team, has claimed responsibility for a cyberattack on an Israeli hospital, resulting in the leak of thousands of medical records, including those of Israeli soldiers.
The breach exposes the global customer base of WALA to potential threats like phishing attacks and financial scams, emphasizing the need for affected parties to monitor their financial accounts and implement additional security measures.
The OPM has launched a new Federal Rotational Cyber Workforce Program, allowing cybersecurity employees in the federal government to apply for rotational opportunities at other agencies to enhance their skills and defend against evolving threats.
The fake plugin, once installed, creates a hidden admin user and sends victim information to the attackers, while also downloading a backdoor payload that allows for file management, SQL client, and server environment information access.
The zero-click RCE bug found in Android’s System component allows attackers to gain arbitrary code execution without user interaction. The bug (CVE-2023-40088) is found in Android’s System component and can be exploited without additional privileges.
Phishing attackers are increasingly using PDF documents to conduct successful campaigns by exploiting the trustworthiness of the file format and leveraging social engineering tactics.
TrickMo replaces screen recording with collecting Accessibility event logs to gather data from running applications, requiring victims to grant Accessibility Service access.