As per Axios, Sequoia Capital told its investors that some of their personal and financial information may have been accessed by a third party, after a Sequoia employee’s email was successfully phished.
The Kroger Co. has advised customers of its pharmacy and Little Clinic of a data security breach in which patient names and sensitive personal information was illegally accessed.
Talos experts uncovered attacks against users in Turkey, Latvia, and Italy, the infections have some similarities with attacks that targeted users in Bulgaria, Lithuania, Hungary, Estonia, Romania, and Spain in September, October, and November 2020.
Regional internet registry RIPE NCC is warning of a credential-stuffing attack against its single sign-on service, RIPE NCC Access, and is encouraging users to implement two-factor authentication (2FA).
The Tor mode included with the Brave web browser allows users to access .onion dark web domains inside Brave private browsing windows without having to install Tor as a separate software package.
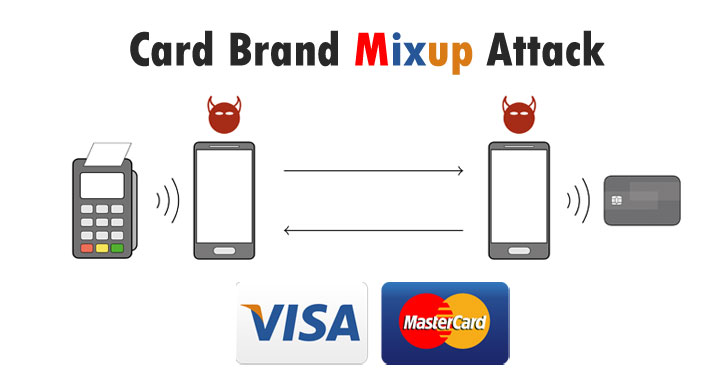
Cybersecurity researchers have disclosed a novel attack that could allow criminals to trick a point of sale terminal into transacting with a victim’s Mastercard contactless card while believing it to be a Visa card.
In response to the attack, officials shut down all computer systems at the Thunder Bay and Orillia campuses. The message sent to faculty members doesn’t say how the threat actors managed to infiltrate the information systems of the university.
UL LLC, better known as Underwriters Laboratories, has suffered a ransomware cyberattack that encrypted its servers and caused them to shut down systems while they recover.
The COVID-19 pandemic is being completely exploited by online scammers. Kaspersky researchers laydown trends and studies for phishing and spam for the past year.
Researchers explain how the DDoS attack trend in the final quarter of the year 2020 is a unique one and highlights what to expect from DDoS threats for Q1 2021.