Along with others, Joseph Garrison stole approximately $600,000 from 1,600 victim accounts by adding a new payment method, depositing $5 into each account, and then withdrawing the funds.
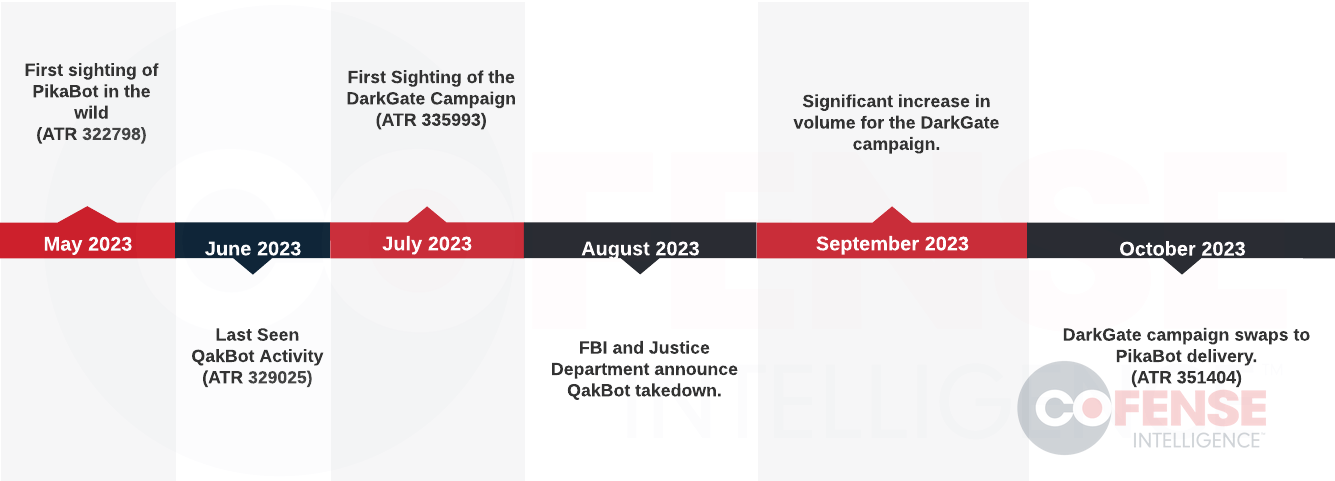
Phishing campaigns are using tactics previously seen in attacks involving the QakBot trojan to deliver malware families such as DarkGate and PikaBot. These campaigns utilize hijacked email threads, unique URL patterns, and a similar infection chain.
The majority of state-sponsored cyberattacks against Russia are believed to originate from North Korea and China, according to a report by Russian cybersecurity firm Solar. This comes as a surprise given the political partnerships between them.
The ICO believes Clearview’s mass scraping of personal information infringes on the data rights of U.K. residents and seeks to overturn the court’s decision to protect their privacy.
The FCC’s proposal comes in response to demands from lawmakers, E-Rate applicants, and school connectivity advocates to address the urgent need for cybersecurity protections in schools and libraries.
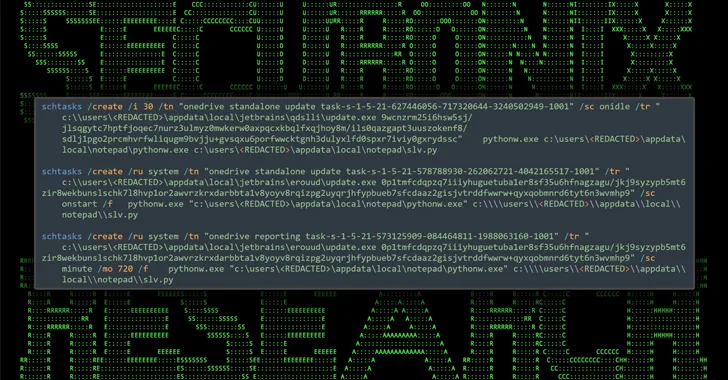
The ultimate goal of the attack is to deceive users into downloading a fake WinSCP installer that contains malware, while also establishing persistence and contact with a remote server.
The attackers posed as a group soliciting donations for children in Palestine, using emotionally charged language and news articles to manipulate recipients. They requested cryptocurrency donations and employed tactics to conceal their identity.
The rule includes exceptions for cases where public disclosure of a cyber incident could pose significant risks to public safety or national security, allowing companies to work with law enforcement agencies to address secret cybersecurity events.
These malicious packages have been downloaded thousands of times, mainly from the U.S., China, France, and other countries. The attacker used steganography to hide a malicious payload within an innocent-looking image file
Regulatory compliance and upcoming regulations, such as the Digital Operational Resilience Act, are driving the need for organizations to engage in threat intelligence sharing.