The campaign leverages multiple vulnerabilities, including command injection, remote code execution, and arbitrary command execution, to gain control of targeted devices and incorporate them into the botnet.
Grayling employs a combination of custom malware and publicly available tools like Havoc, Cobalt Strike, and NetSpy to carry out its attacks, using DLL sideloading techniques and exploiting vulnerabilities like CVE-2019-0803.
Air Europa suffered a cyberattack on its online payment system. While there is no evidence of fraudulent use, customers are warned to replace their bank cards as a precautionary measure.
Gutsy, a cybersecurity startup founded by the team behind Twistlock, has emerged from stealth with a $51 million seed round led by YL Ventures and Mayfield. The company applies process mining, a data science technique, to cybersecurity.
As per the investigations, the ongoing fraud came to light after a complaint that some individuals had allegedly hacked into the six-year-old firm’s payment gateway, and the funds were then transferred to at least 260 different bank accounts.
The campaign employs a multi-stage attack chain to capture sensitive information entered on checkout pages and exfiltrate it to a remote server, making it difficult to detect.
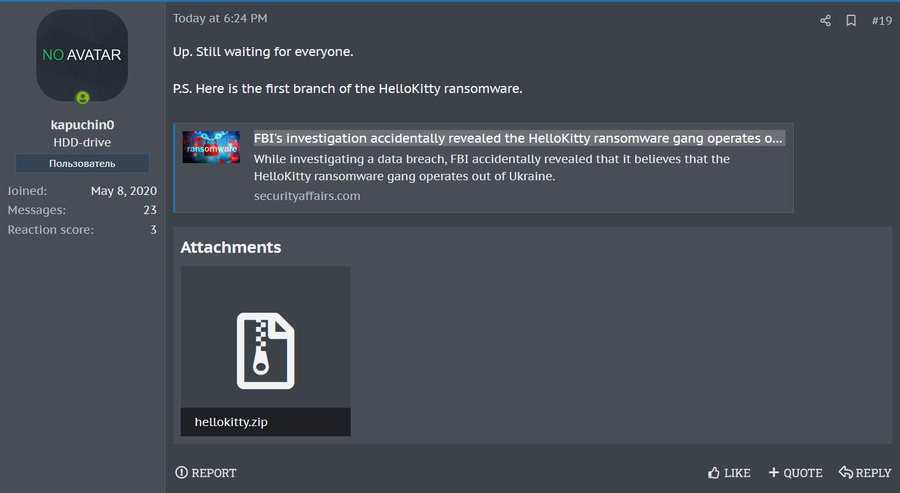
The source code for the first version of the HelloKitty ransomware has been leaked on a Russian-speaking cybercrime forum. The threat actor, known as ‘kapuchin0’, claims to be developing a more powerful encryptor.
Caesars Entertainment has confirmed that a social engineering attack on an outsourced IT support vendor led to a data breach, impacting tens of thousands of its customer rewards program members.
Millennial and Gen Z workers exhibit more unsafe cybersecurity habits compared to older age groups, such as using the same passwords on multiple devices and sharing work devices with family and friends.
Google’s research team has launched v8CTF, a capture-the-flag (CTF) challenge focused on its Chrome browser’s V8 JavaScript engine. The competition opened on October 6, 2023, and is accessible to any exploit writers.