Threat actors behind RedLine and Vidar have streamlined their operations by adding well-established tactics to deceive victims. The victim initially receives an info stealer with Extended Validation (EV) code signing certificates, but later starts receiving ransomware payloads through the same channel. Experts advise organizations to adopt a proactive approach to thwart attacks early in the threat […]
Researchers have uncovered fresh malware samples attributed to ransomware group Cuba, representing new versions of BurntCigar malware, which offers next-level stealth to the group.
The funding will launch its GenAI Identity fraud solution out of stealth and help the company scale to prevent large-scale SuperSynthetic identity fraud across multiple verticals, including the financial service industry, fintech, and e-commerce.
The campaign uses batch files distributed via Facebook messages, utilizing images of defective products as bait, and stealing credentials and cookies from multiple browsers, not just Facebook, increasing the risk of targeted attacks.
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has announced it is offering free security scans for critical infrastructure facilities, such as water utilities, to help protect these crucial units from hacker attacks.
This scenario calls for establishing trust in all enterprise access entities, data sources, and computing services through secure communication and the validation of access policies.
The company has announced today that it’s experiencing issues with its HOP services (integrated ticketing and fares system) as a cyber incident has impacted parts of its network.
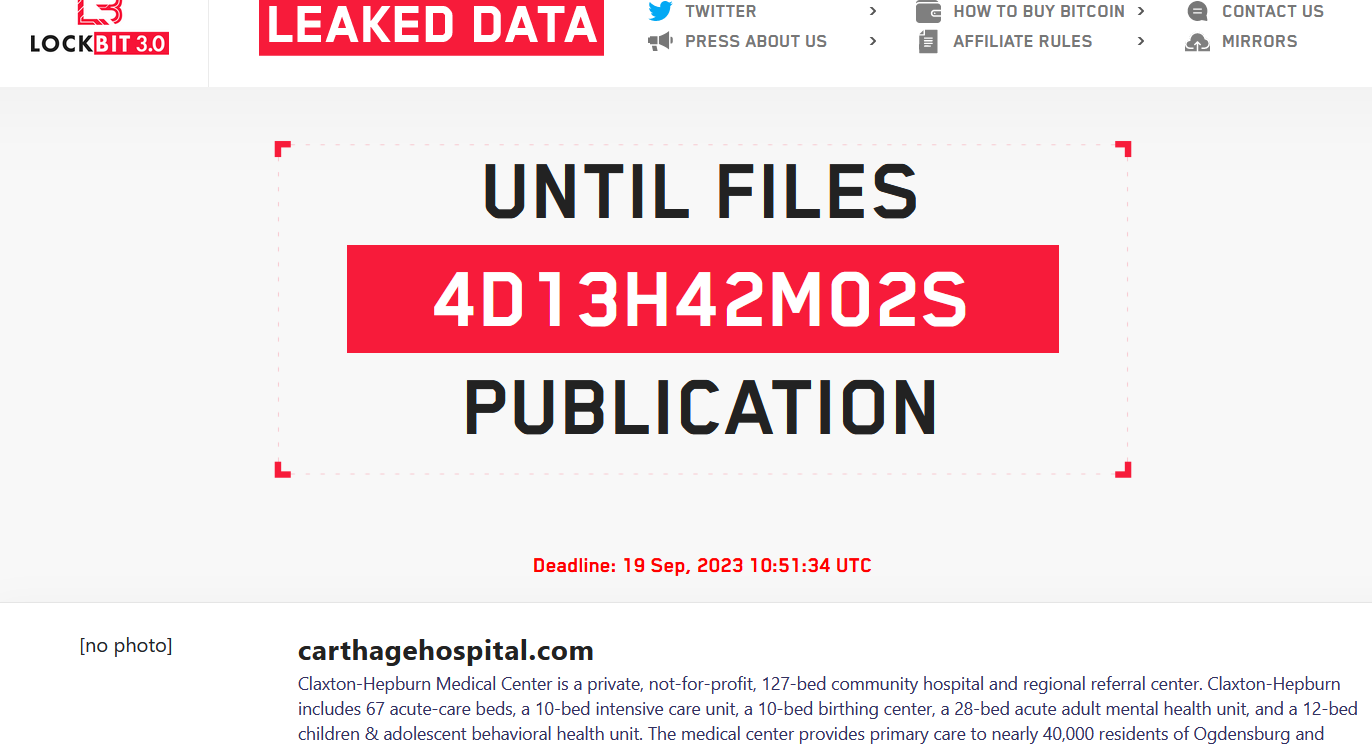
The Lockbit ransomware group claims to have hacked two major hospitals, the Carthage Area Hospital and Claxton-Hepburn Medical Center. The two hospitals serve hundreds of thousands of people in upstate New York.
The group used AzureHound and Roadtools to conduct reconnaissance in Microsoft Entra ID (formerly Azure Active Directory) environments and deployed multiple persistence mechanisms including the use of Azure Arc.
The malware targets Microsoft users and steals various types of data, including email credentials, payment card information, and cryptocurrency passwords. It is particularly appealing to less technically skilled individuals due to its ease of use.