A revised data breach notification is being sent to victims stating that attackers may have also stolen their credit/debit card number, beyond the raft of personal information.
The activities observed suggest the threat actor intends to perform espionage and maintain access to organizations across a broad range of industries for as long as possible.
In H1 2023, compromised credentials accounted for 50% of root causes, whereas exploiting a bug came in at 23%. We can’t conclusively say that attackers are favoring compromised credentials over vulnerabilities, but it can’t be denied either.
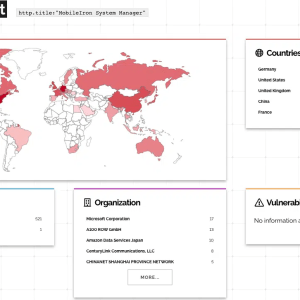
The vulnerability could be exploited to access sensitive API data and configurations, run system commands, or write files onto the system. The vulnerability CVE-2023-38035 impacts Sentry versions 9.18 and prior.
Malicious actors are targeting Roblox developers with a new malware called Luna Grabber, distributed through npm packages that impersonate legitimate software. These fake packages, including noblox.js-vps, noblox.js-ssh, and noblox.js-secure, house malicious multi-stage payloads. This campaign underscores the recurring strategy of threat actors employing typosquatting as a tactic to deceive developers.
In a public statement published on August 23, 2023, Pôle emploi confirmed “a breach in the information system of one of its service providers, involving a risk of disclosure of jobseekers’ personal data.”
Despite the shutdown of certain internal systems following the detection of unusual network activity, SRHS disclosed that workarounds have been implemented to ensure the partial continuation of business operations.
Whiffy Recon works by checking for the WLAN AutoConfig service (WLANSVC) on the infected system and terminating itself if the service name doesn’t exist. Persistence is achieved by means of a shortcut that’s added to the Windows Startup folder.
The exact origins of the threat actors, dubbed Neanderthals, are unclear, but evidence points to Russia as the country of origin of the toolkit’s authors and users, owing to the use of Russian SMS templates.
QuiteRAT is clearly an evolution of MagicRAT. While MagicRAT is a bigger, bulkier malware family averaging around 18MB in size, QuiteRAT is a much much smaller implementation, averaging around 4 to 5MB in size.