Implementing a nimble incident response process and establishing repeatable procedures for investigations are crucial for reducing the impact of data breaches and minimizing legal repercussions.
A sweeping partnership comprising nine government agencies and over 200 nonprofits, corporations, colleges, and universities will together build an organized “whole of society” approach to expanding the cybersecurity workforce, the ONCD announced.
WikiLoader is a sophisticated downloader malware that evades detection and is likely available for sale to multiple cybercriminal groups. It has been observed in multiple campaigns targeting Italian organizations.
BleedingPipe is a vulnerability found in many Minecraft mods caused by the incorrect use of deserialization in the ‘ObjectInputStream’ class in Java to exchange network packets between servers and clients.
“Cyber education and workforce development have not kept pace with demand and the rapid pace of technological change,” says the strategy document. “Moreover, skills in demand in the cyber workforce are evolving.”
For every 10,000 enterprise users, an enterprise organization is experiencing approximately 183 incidents of sensitive data being posted to ChatGPT per month, according to Netskope.
The Call of Duty: Modern Warfare 2 servers were taken offline due to the presence of a self-spreading worm virus targeting PC gamers. Hackers used hacked lobbies to spread the malware, infecting multiple players’ devices with the virus.
The provider of health, dental, and wellness benefits at the University of Guelph (U of G) has begun notifying students of a data breach which included access to personal information.
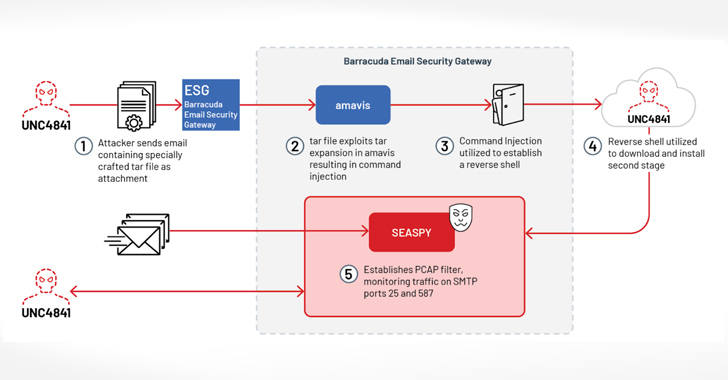
“SUBMARINE comprises multiple artifacts — including a SQL trigger, shell scripts, and a loaded library for a Linux daemon — that together enable execution with root privileges, persistence, command and control, and cleanup,” the agency said.
The Dark Power ransomware exploits vulnerabilities in kernel-related APIs to quickly propagate through the cyber-kill chain. It also leverages DLLs such as kernel32.dll, bcrypt.dll, and ole32.dll to carry out its malicious activities.