Now tracked as CVE-2023-38750, the security flaw is a reflected Cross-Site Scripting (XSS) discovered by security researcher Clément Lecigne of Google Threat Analysis Group.
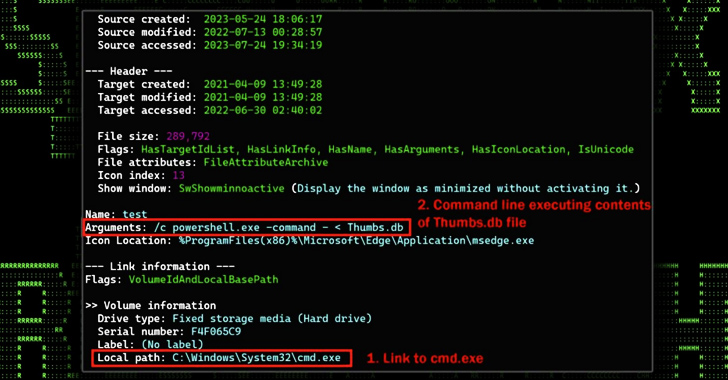
An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S. Military-themed document lures to trick them into running malware on compromised systems.
Researchers at Patchstack discovered and disclosed the three vulnerabilities to the plugin’s developer, Saturday Drive, on June 22nd, 2023, warning that it affects NinjaForms versions 3.6.25 and older.
A legitimate Windows search feature could be exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT.
A recently detected malvertising campaign, known as Nitrogen, has been discovered exploiting Google Search and Bing ads to target users searching for IT tools. The Nitrogen campaign predominantly focuses on technology and non-profit organizations in North America. It operates by posing as installers for well-known software such as AnyDesk, Cisco AnyConnect VPN, TreeSize Free, and […]
The vulnerability, tracked as CVE-2023-24489 (CVSS score of 9.1), was the result of errors leading to unauthenticated file upload, which could then be exploited to obtain RCE, says security firm Assetnote, which identified and reported the bug.
Given the potentially serious repercussions of shadow IT, technical teams should focus on finding where it exists in the organization and addressing the underlying causes of it, the NCSC argued.
An investigation by ReversingLabs researchers has uncovered evidence of more malicious npm packages, with links to the same infrastructure that also appear to target cryptocurrency providers.
“On July 22nd, CoinsPaid experienced a hacker attack, resulting in the theft of USD 37.3M,” reads the announcement published by the company. “We believe Lazarus expected the attack on CoinsPaid to be much more successful.”
The Global Times newspaper, owned by the Chinese Communist Party, reported on July 26 that the Wuhan Municipal Emergency Management Bureau revealed that the Monitoring Center had been subjected to a cyberattack by an “overseas organization.”