The infection chain is triggered by the exploitation of vulnerable on-premises Internet Information Services (IIS) and Microsoft Exchange serves to infiltrate target networks.
The Palo Alto company said the $15 million Series A was led by U.S. Venture Partners (USVP) and Foundation Capital, two prominent investment firms betting on cybersecurity startups.
The malware, rented for $150/month, targets 40 web browsers, 70 browser extensions, 21 cryptocurrency applications, 9 MFA and password management applications, 55 cryptocurrency browser extensions, Steam and Telegram credentials, and more.
Security experts at ESET stumbled across an updated version of the Android GravityRAT spyware being distributed under the disguise of messaging applications such as BingeChat and Chatico. The BingeChat campaign is ongoing since August 2022, whereas the Chatico campaign doesn’t seem active anymore. GravityRAT can extract WhatsApp backups and receive commands for file deletion.
The US Department of Agriculture is investigating a “possible data breach” of a department contractor connected to a broader hack on multiple federal agencies that officials have blamed on Russian cybercriminals, a spokesperson told CNN.
Polish police officers of the country’s Central Bureau for Combating Cybercrime detained two suspects believed to have been involved in operating a DDoS-for-hire service (aka booter or stresser) active since at least 2013.
Due to the complexity of the hardware supply chain, encryption chips sold by the subsidiary of a company flagged in the Entity List have found their way into the storage hardware of military and intelligence networks across the West.
Cyberattacks using malicious lookalike domains, email addresses, and other types of registered identifiers are rising, domain name system (DNS) security provider Infoblox found.
A report published Wednesday by the Atlantic Council’s Cyber Statecraft Initiative asserts that the SEC’s proposed rules — requiring incident disclosure within four days — substantially differ from CIRCIA regulations.
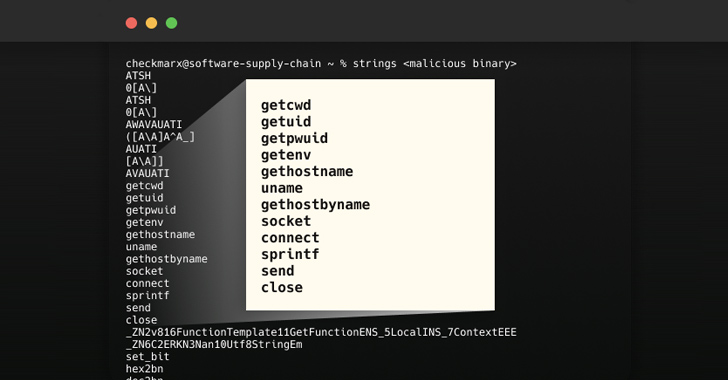
In what’s a new kind of software supply chain attack aimed at open-source projects, it has emerged that threat actors could seize control of expired Amazon S3 buckets to serve rogue binaries without altering the modules themselves.