After a major lull in CVEs addressed last month, expect Microsoft to be back on track with their annual averages for both their operating systems and Office application updates next week.
The attack involved only the theft of files rather than theft followed by encryption. After exfiltrating hundreds of files, the attacker then uploaded thousands of PREVENT-LEAKAGE.txt files.
A previously undisclosed backdoor named Stealth Soldier is targeting Libyan organizations. Security experts have identified three distinct infection chains involving three different versions of Stealth Soldier malware. The recent campaign underscores the growing complexity of cyberespionage activities.
Hyundai and Kia cars were stolen 977 times in New York City in the first four months of 2023, and authorities have had enough. This represents a roughly 660 percent increase in such thefts as compared to those same months in 2022.
In a press conference on June 8, ACT government chief digital officer Bettina Konti said there is a likelihood that some personal information is involved but the harms assessment needs to be completed for that to be clear.
Onur Aksoy, 39, of Miami, pleaded guilty to conspiring with others to traffic in counterfeit goods, to commit mail fraud, and to commit wire fraud and mail fraud. He made over $100m from importing and selling counterfeit Cisco networking devices.
Security researchers are warning about a bug in the Microsoft Visual Studio installer that gives cyberattackers a way to create and distribute malicious extensions to application developers, under the guise of being a legitimate software publisher.
Progress Software warned customers today of newly found critical SQL injection vulnerabilities in its MOVEit Transfer managed file transfer (MFT) solution that can let attackers steal information from customers’ databases.
Following yesterday’s attack, multiple major banks across Russia had their access cut off from the country’s banking systems so that they can no longer make online payments, as Ukrainian news site Economichna Pravda first reported.
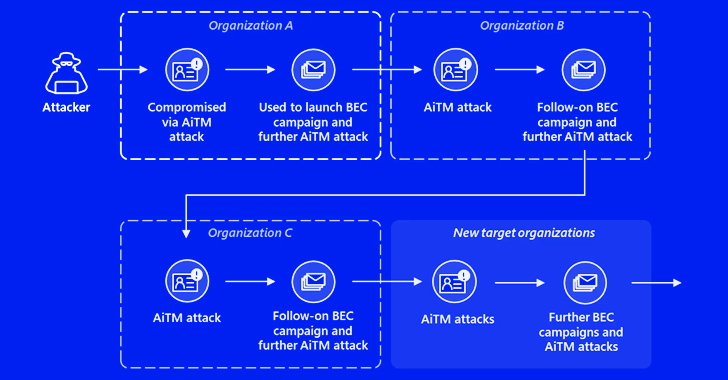
“The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations,” the tech giant disclosed in a Thursday report.