Dubbed “VIP Invoice Authentication Fraud” by Armorblox, the tactic is used in classic fake emails designed to impersonate trusted vendors or other third parties that the victim organization regularly pays.
The $60 million Series C was led by Sapphire Ventures and brings the total raised by Huntress to a whopping $118 million. Existing investors JMI Equity and Forgepoint Capital expanded their equity stake.
For the last two weeks, the city has been engulfed in a massive recovery effort after the Royal ransomware gang caused significant damage to systems that manage the city’s police, fire department, courts, critical infrastructure, and more.
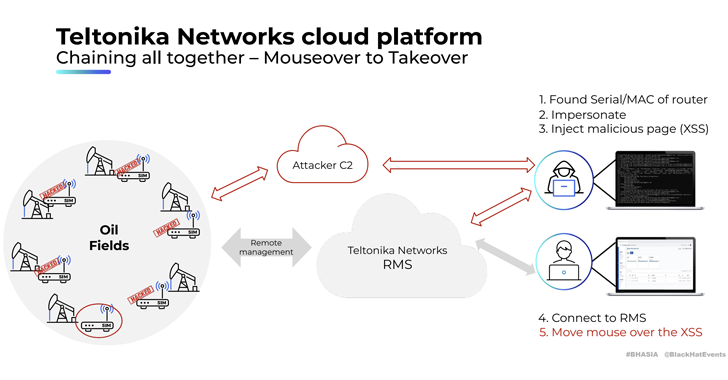
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors that could expose operational technology (OT) networks to external attacks.
The threat actor known as Water Orthrus was spotted with two new campaigns in March and April 2023 that intended to deliver CopperStealth and CopperPhish payloads. The new malware have been upgraded for different purposes, such as injecting network advertisements, acquiring personal information, and stealing crypto assets. Organizations must leverage the updated IOCs associated with the […]
As the rate of cyberattacks steadily increases, automated threat hunting processes are being integrated to help stem the tide by providing quicker security insights, more efficient operations, and human error reductions.
Cybersecurity experts took the wraps off of a newer variant of BPFDoor (BPF stands for Berkeley Packet Filter), which is capable of maintaining persistent access to breached systems for extended periods. The new variant has remained entirely undetected by all the virus-detection engines on VirusTotal. To mitigate the risks associated with BPFDoor, admins should prioritize […]
SentinelLabs detected 10 ransomware families employing VMware ESXi lockers, derived from the leaked 2021 Babuk source code. These variants emerged between H2 2022 and H1 2023. The report also highlights similarities between Babuk’s source code and the ESXi encrypters used by Conti and REvil, indicating some connection between them.
The group is swiftly expanding its operations. To date, it has compromised three organizations in the U.S. and one in South Korea across several business verticals, including manufacturing, wealth management, insurance providers, and pharmaceuticals.
The Illinois Department of Healthcare and Family Services (HFS) and Department of Human Services (IDHS) have disclosed a data breach within the State of Illinois Application for Benefits Eligibility (ABE) system’s Manage My Case (MMC) portal.