While CrowdStrike suspects a North Korean state-backed hacking group it tracks as Labyrinth Collima is behind this attack, Sophos’ researchers say they “cannot verify this attribution with high confidence.”
Mandiant identified a North Korean threat actor, named APT43, conducting cyberespionage campaigns against government organizations in the U.S. and South Korea. Besides its own, APT43 leverages its own set of custom malware, such as Pencildown, Venombite, Pendown, Laptop, Hangman backdoor, and others, not used by other attackers.
The company’s founders argue that an organization’s identity surface is now the number one attack vector, yet as companies increasingly rely on an ever-growing number of third-party services, that’s also becoming increasingly hard to manage.
Over the past few months, threat actors have been spreading ShellBot and Moobot malware on exploitable servers. Compromised victims can be controlled and used as DDoS bots after receiving a command from a C2 server.
MacStealer is a new information-stealing malware threat attempting to pilfer sensitive information from compromised macOS devices. The malware uses Telegram as its C2 channel and specifically affects devices running Catalina and later versions on M1 and M2 CPUs. It can harvest documents, browser cookies, and login information from individuals.
As seen with past attacks from this group, these most recent attacks do not seem to be originating from a single botnet, and the attack methods and sources seem to vary, suggesting the involvement of multiple individual threat actors.
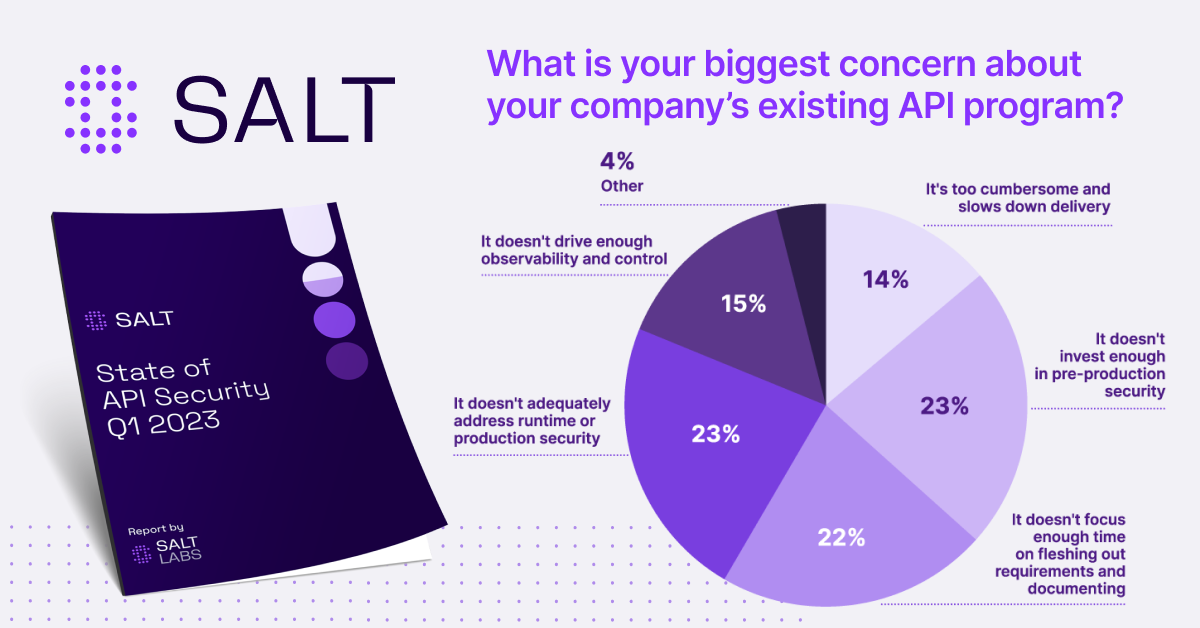
The report also found that 80% of attacks happened over authenticated APIs, making it a widespread problem for all. Given that it is one of the easiest types of attack to execute, it is no surprise that attackers are increasingly taking this route.
ENISA says the three dominant threats to the transportation sector are ransomware (38 percent), data-related threats (30 percent), and malware (17 percent). However, each subgroup has reported experiencing other attack types than ransomware.
In this blog, researchers have shared details about two distinct campaigns that used various 0-day exploits against Android, iOS, and Chrome and were both limited and highly targeted.
Mélofée’s features are no different from other backdoors of its kind, enabling it to contact a remote server and receive instructions that allow it to carry out file operations, create sockets, launch a shell, and execute arbitrary commands.