The Israeli startup said the financing was provided by StageOne Ventures, First Rays Venture Partners, and D. E. Shaw & Co. A roster of prominent security practitioners and entrepreneurs also joined the round.
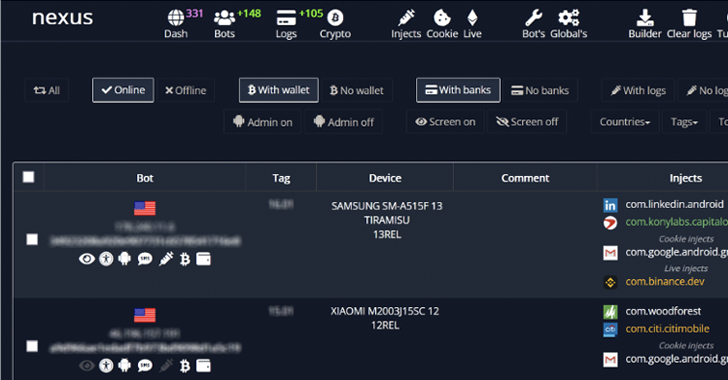
“Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception,” Italian cybersecurity firm Cleafy said.
The US Cybersecurity and Infrastructure Security Agency (CISA) this week announced adding more experts to its Cybersecurity Advisory Committee (CSAC) and updating the baseline cybersecurity goals introduced last year.
A joint cybersecurity advisory from the German Federal Office for the Protection of the Constitution (BfV) and the National Intelligence Service of the Republic of Korea (NIS) warn about Kimsuky’s use of Chrome extensions to steal Gmail emails.
The hearing comes as Congress weighs legislation that would empower the Biden administration to ban TikTok along with other foreign apps that many politicians in Washington and around the country say pose a U.S. national security threat.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released eight Industrial Control Systems (ICS) advisories on Tuesday, warning of critical flaws affecting equipment from Delta Electronics and Rockwell Automation.
Security researcher abel took the wraps off Emotet’s new distribution technique that allows it to propagate through Microsoft OneNote email attachments. The operators have a history of deploying malicious macros on infected systems via Microsoft Word and Excel attachments. This new method of infection will help criminals dodge Microsoft security checks and infect more targets.
Tens of thousands of documents containing personal information of special education students within New York City’s public school system were held in an unsecured database exposed to the internet.
The email was spoofed to appear as if sent from the SVP and general counsel of a trusted, long-term partner company of the targeted enterprise, according to Abnormal Security.
Trigona ransomware, which surfaced in December 2022, targeted at least 15 organizations across different sectors in the U.S., Australia, Italy, France, New Zealand, and Germany. The malware is capable of getting initial access, performing reconnaissance, transferring malware via a remote monitoring and management software, creating new user accounts, and dropping ransomware.