The settlement benefits consumers who received a data breach notification from Orlando Family Physicians informing them their personal information or protected health information may have been compromised in a data breach on April 15, 2021.
CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an “evolution or direct rebrand” of another ransomware strain known as Pandora based on code-level similarities.
Investments in cybersecurity are expected to reach nearly $300 billion in 2026, driven by the ongoing threat of cyberattacks, the demands of providing a secure hybrid work environment, and the need to meet data privacy and governance requirements.
The ransomware group added the company to its Tor data leak site and announced the theft of stolen private and personal confidential data, employee IDs, passports, contracts, etc.
According to a Huntress report, 49% of mid-sized businesses plan to budget more for cybersecurity in 2023. 61% of mid-sized businesses do not have dedicated cybersecurity experts in their organization.
Discovered in or around the beginning of March, the Microsoft Outlook vulnerability was found to affect several applications from the Microsoft 365 Apps Enterprise stack, including MS Office 2019, 2016, 2013, and LTSC.
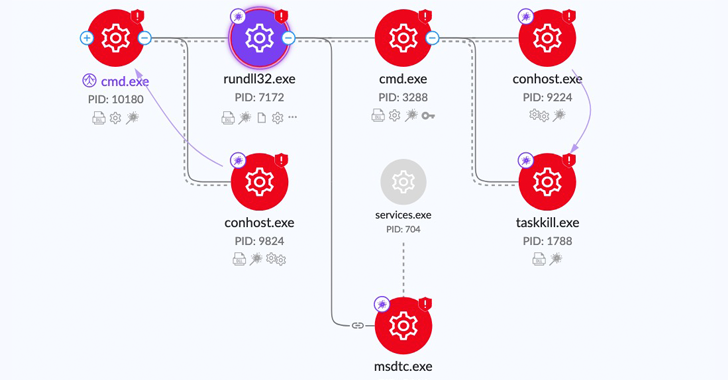
The attacker’s actions had the whiff of a Black Basta affiliate, with Qbot activity widely reported as being a cornerstone of Black Basta intrusions. Black Basta is a splinter group that emerged after the “Conti” ransomware syndicate was quelled.
Hitachi Energy immediately launched an investigation into the incident and disconnected the compromised system. The company reported the data breach to law enforcement agencies and data protection watchdog.
Also referred to as LockBit Black, LockBit 3.0 has a more modular architecture compared to its previous variants, and supports various arguments that modify its behavior after deployment.
Chinese hackers exploited a critical Fortinet bug and used custom networking malware to steal credentials and maintain network access, according to Mandiant. Victims include defense, telecom, and technology firms, as well as government agencies.