Much like other cyberattacks, malicious actors carry out SQL injection attacks in various stages across the attack life cycle. During an SQL injection attack specifically, attackers use a wide variety of techniques to gain access to their targets.
Microsoft researchers released in-depth analyses of the threat ecology of the Russian-affiliated Nobelium group and how it exploited MagicWeb to perform a complex authentication bypass for Active Directory Federated Services (AD FS). Microsoft first spotted MagicWeb in August 2022, when a Microsoft customer fell victim to a post-compromise capability of MagicWeb.
Recently, Kaspersky researchers shared with VPNOverview details of two separate campaigns — a scam designed to inject PCs with malware and a phishing ploy designed to steal banking information and other financial data.
Hackers are sending tailored phishing messages to their intended targets by language and location via geotargeting tool known as Geo Targetly, according to Avanan. The threat actors have been following the spray-and-pray technique that ensures they can target a massive number of individuals in one go. As phishing attacks keep evolving, organizations and individuals should […]
In January, cybersecurity company Sonatype said it found 691 malicious npm packages and 49 malicious PyPI components containing crypto-miners, remote access Trojans (RATs), and more.
A new joint advisory warns of North Korean hackers that are involved in ongoing ransomware attacks against healthcare systems in South Korea and the U.S. According to the advisory, the modus operandi of the attacks includes North Korean hackers acquiring and purchasing infrastructure to conceal their identities. The cybersecurity agencies have shared a list of recommendations […]
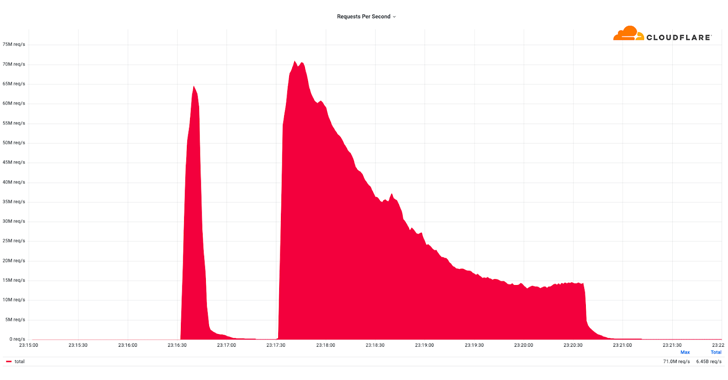
“The majority of attacks peaked in the ballpark of 50-70 million requests per second (RPS) with the largest exceeding 71 million,” Cloudflare said, calling it a “hyper-volumetric” DDoS attack.
New findings from researchers at the security firm Sophos show how pig butchering scammers are tweaking and refining their strategies to try to ensnare more unsuspecting victims.
As part of the $1.2 trillion infrastructure spending deal signed into law last year, $1 billion was allocated to state and local governments to upgrade their cybersecurity defenses.
North Korean hackers have found a way around U.S.-imposed sanctions to launder the cryptocurrency proceeds from their heists, according to evidence discovered by blockchain analysts.