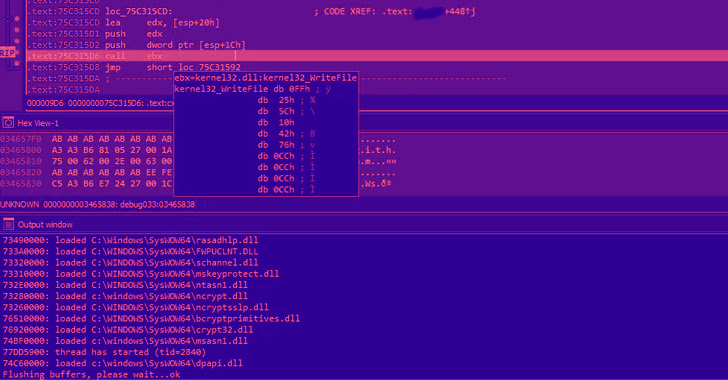
A newly identified CatB ransomware group has been found implementing several anti-VM and DLL hijacking techniques to evade detection. Before activating anti-evasion techniques, the malware checks for a processor’s core, hard drive size, and physical memory of targeted machines. The ransomware is believed to have a connection with Pandora ransomware.
The Housing Authority of the City of Los Angeles (HACLA) has confirmed that it is dealing with a cyberattack after the agency appeared on the leak site of the LockBit ransomware group.
Taiwan-based networking and storage solutions provider Synology has informed customers about the availability of patches for several critical vulnerabilities, including flaws likely exploited recently at the Pwn2Own hacking contest.
The unknown adversary is believed to have hijacked the IT infrastructure of a Colombian cooperative bank, using the information to craft convincing decoy messages to lure victims into opening suspicious Excel attachments.
An analysis conducted by SecurityWeek shows that more than 290 vulnerabilities were patched in HarmonyOS in 2022, including nearly 100 security flaws affecting third-party libraries.
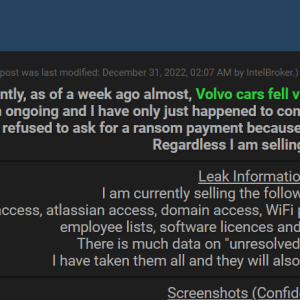
Researcher Anis Haboubi yesterday first noticed that a threat actor was attempting to sell data allegedly stolen from Volvo Cars on a popular hacking forum. A forum member claimed on December 31, 2022, that it fell victim to a ransomware attack.
PyTorch team has identified a malicious dependency within its framework library. The package was the homonym for the torchtriton dependency. Exploiting it, a hacker could successfully trigger dependency confusion attacks, compromising multiple systems. PyTorch admins advised users to uninstall the counterfeit framework.
Financial and insurance sectors in Europe have been targeted by the Raspberry Robin worm, as the malware continues to evolve its post-exploitation capabilities while remaining under the radar.
Many companies don’t realize just how intertwined we are with our suppliers nowadays. Most of the software and data we rely upon today are no longer on our devices; they are in someone else’s server, data center or cloud.
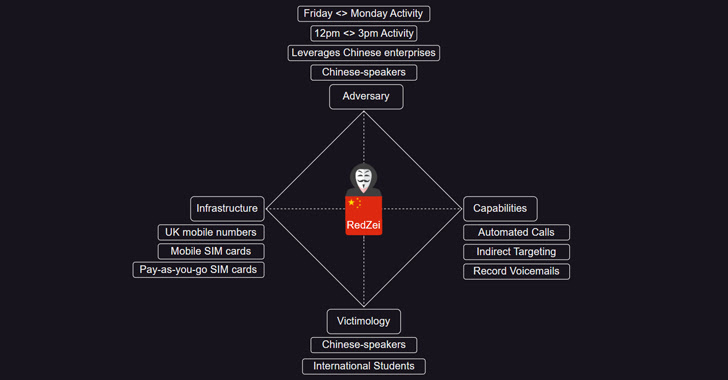
Chinese international students in the U.K. have been targeted by persistent Chinese-speaking scammers for over a year as part of an activity dubbed RedZei (aka RedThief).