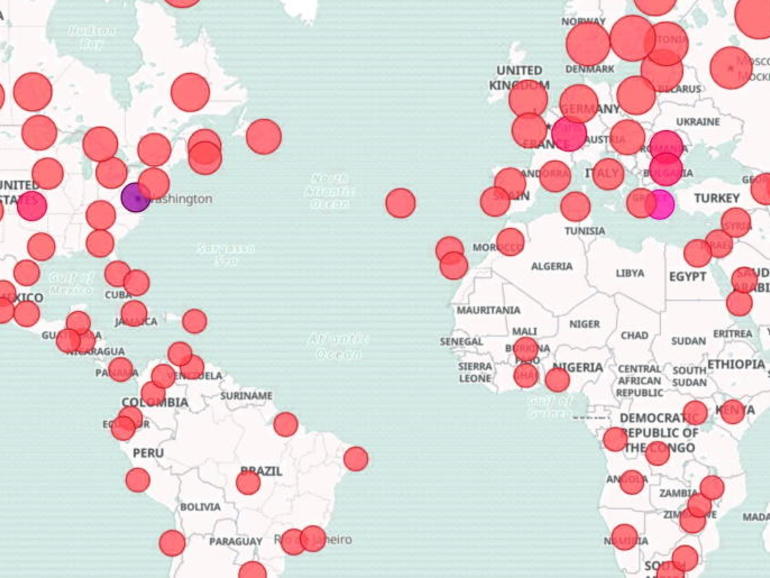
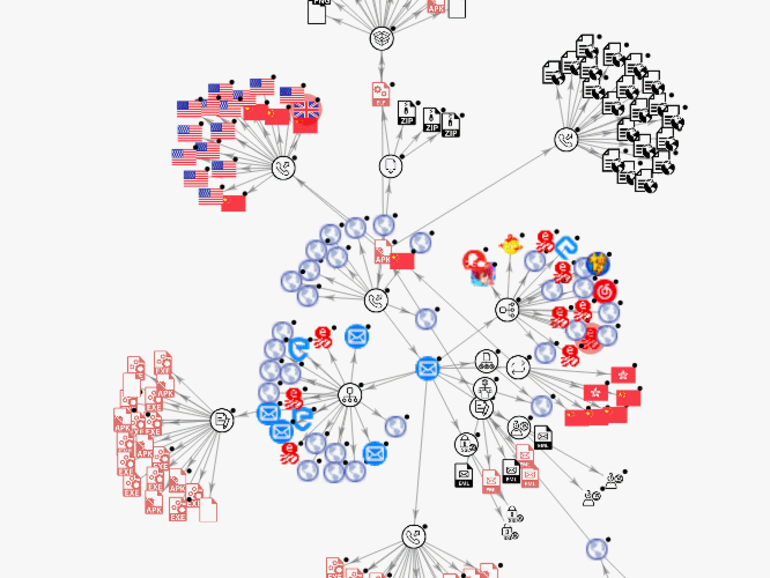
A malicious spam campaign that targeted over a hundred thousand users a day over Christmas and New Year has seen Emotet secure its spot as the most prolific malware threat.
Secretary of State Mike Pompeo announced on Thursday the creation of a new bureau inside the US Department of State dedicated to addressing cybersecurity as part of the US’ foreign policy and diplomatic efforts.
Researchers are warning that several cyber gangs have started infecting Linux machines via a fileless malware installation technique that until recently was more commonly used against Windows-based systems.
CISA said that the threat actor behind the SolarWinds hack also used password guessing and password spraying attacks to breach targets as part of its recent hacking campaign and didn’t always rely on trojanized updates as its initial access vector.
Researchers have linked the botnet to a cybercrime operation known as TeamTNT; a group first spotted over the 2020 summer installing cryptocurrency-mining malware on misconfigured container platforms.
Researchers uncovered a new ransomware family called Babuk that has successfully encrypted systems of at least five online gambling companies in the first half of 2020.
Security researchers shed a light on an investigation report involving financially-motivated ransomware actors from China targeting multiple companies.
Cybersecurity researchers revealed a new QRat malspam campaign purporting to contain a scandalous video of the U.S. President Donald Trump.
The penetration testing toolkits have been used to host more than a quarter of all the malware C&C servers deployed in 2020, threat intelligence firm Recorded Future said in a report today.
The fake messages impersonate payment, package delivery and streaming services, government and healthcare organizations, popular IT providers, online retailers, hospitality organizations, and so on.