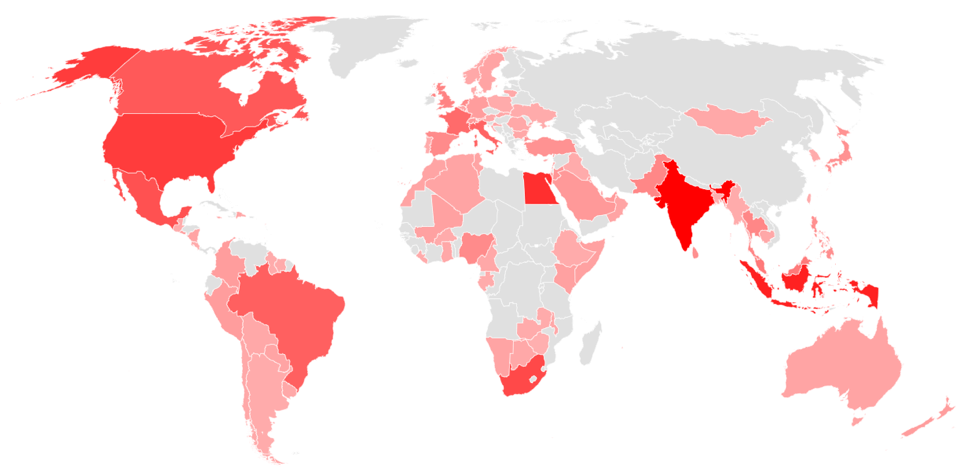
This month, Trickbot ranks as most popular malware impacting 3% of organizations globally, closely followed by XMRig and Qbot which also impacted 3% of organizations worldwide respectively.
The investigation led to the discovery of a new group called “Netbounce” and it exposed their malware delivery infrastructure. What made this stand out is their unique set of tools and techniques.
Ransomining lets threat actors take over computing power to mine cryptocurrency — in this case Monero — and also encrypts the data to hold for ransom, thereby doubling the threat factor.
Cyberattacks have become increasingly sophisticated in the past year, with the SolarWinds hack unlikely to be an isolated event, according to VMware’s 2021 Global Cybersecurity Outlook report.
Two examples of lingering issues that have impacted organizations in 2020 are CVE-2006-1547 and CVE-2012-0391, which are both Apache Struts vulnerabilities which are among the most exploited.
Datto announced that it has acquired BitDam. BitDam’s cyber-defense platform secures collaboration tools, such as M365 and Google Workspace, from ransomware, malware, and phishing.
Security and automation vendor F5 has warned of seven patch-ASAP-grade vulnerabilities in its Big-IP network security and traffic-grooming products, plus another 14 vulnerabilities worth fixing.
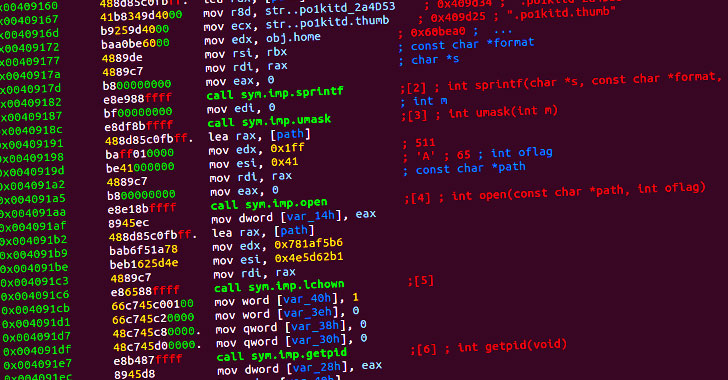
Cybersecurity researchers on Wednesday shed light on a new sophisticated backdoor targeting Linux endpoints and servers that’s believed to be the work of Chinese nation-state actors.
A total of 15 vulnerabilities affecting Netgear switches that use the ProSAFE Plus configuration utility were found to expose users to various risks, according to researchers with NCC Group.
The attack affected IT systems at a Spanish government agency that manages unemployment benefits, disrupting “hundreds of thousands” of appointments at the agency, a Spanish labor union said Tuesday.