Cybercrime against digital media and entertainment organizations is on the rise. Hackers formulate new and innovative ways to defeat security measures and controls to pilfer sensitive data.
Guardicore first spotted the attack back in January 2020. After that, it witnessed a total of 92 attacks emanate from 11 IP addresses, with most based in Ireland and the UK at the time of analysis.
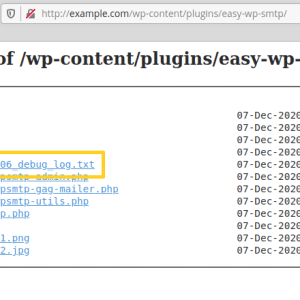
The zero-day vulnerability affects WP SMTP 1.4.2 and earlier versions, it resides in a feature that creates debug logs for all emails sent by the site and store them in the installation folder.
It’s still unclear what kind of information might have been compromised. Much of the city’s files — budget documents, building plans, and council minutes — are records available to the public under the Missouri Sunshine Law.
The new code-injection technique essentially allows cybercriminals to inject code to launch dangerous XSS (cross-site scripting) attacks within the bounds of a PDF document.
Retailers are on high alert during the holiday season of Magecart attacks, which implant malicious computer code into websites and third-party suppliers of digital systems to steal credit card info.
ESET researchers discovered that chat software called Able Desktop, used by 430 government agencies in Mongolia, was used to deliver the HyperBro backdoor, the Korplug RAT, and a RAT called Tmanger.
Computers hacked at Italian defense group Leonardo between 2015 and 2017 belonged to a unit that makes components for both commercial and military aircraft, including C27J and ATR turboprop, a police officer working on the case told Reuters.
Samsung has started rolling out Android’s December security updates to mobile devices to patch critical security vulnerabilities in the operating system and related components.
Microsoft Office, this month the company released 23 security updates and 5 cumulative updates for 7 different products, fixing 9 vulnerabilities that could allow attackers to execute arbitrary code remotely on vulnerable systems.