Threat actors are bypassing Google’s security measures and using fingerprinting techniques to ensure successful execution of malicious downloads, pointing to a potential “malvertising as a service” model.
Researchers have discovered a new multi-platform threat called NKAbuse that uses a decentralized network connectivity protocol called NKN to communicate. NKAbuse leverages blockchain technology to conduct DDoS attacks and function as an implant.
The 8220 gang, a Chinese-origin threat actor, continues to target Windows and Linux web servers with cryptojacking malware using evolving tactics and known vulnerabilities.
Ledger users are advised to avoid using web3 dApps following a supply chain attack on the Ledger dApp Connect Kit library, which resulted in the theft of $600,000 worth of crypto and NFTs.
The ALPHV ransomware gang is facing technical difficulties, with their leak site showing only one victim and negotiation links not working, potentially leaving them without payment.
The emergence of ten new Android banking malware families in 2023 highlights the increasing sophistication and capabilities of these trojans, including automated transfer systems, social engineering tactics, and live screen-sharing capabilities.
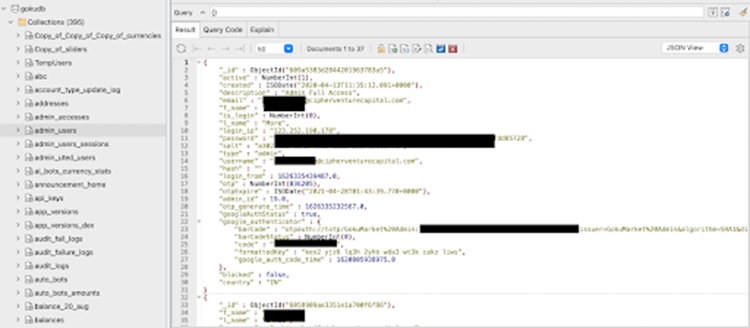
The centralized crypto exchange GokuMarket, owned by ByteX, left an open instance, exposing sensitive user data, including IP addresses, email addresses, encrypted passwords, and crypto wallet addresses.
The IT network of New York-based health providers, including HealthAlliance Hospital, Margaretville Hospital, and Mountainside Residential Care Center, was breached for nearly two months, resulting in the compromise of patient data.
The Federal Communications Commission (FCC) has updated its data breach rules for the first time in 16 years. The new rules expand the definition of a breach and specify who should be notified.
Karakurt uses various tactics to steal data and extort victims for ransom. They contact victims’ employees, business partners, and clients to pressure them into paying the ransom.