“We were recently contacted by a ransomware group who claimed they have illegally obtained a limited number of Crown files,” a spokesperson of the formerly listed firm said in a statement.
ChatGPT’s ability to draft highly realistic text makes it a useful tool for phishing purposes. In addition to generating human-like language, ChatGPT is capable of producing code in a number of different programming languages.
The campaign targets manufacturing companies and multiple businesses in European countries through phishing emails. The malicious payload is distributed through WordPress sites with authorized SSL certificates.
Security researchers at Proofpoint described the malware samples in an advisory published on Monday, which names them Standard, Lite, and Forked IcedID variants respectively.
Shadow IT teams, also known as rogue IT teams, have grown in popularity in recent years due to the rise of cloud-based apps and remote work. However, this has led to operational tension and security risks within many businesses.
The NullMixer package is including new polymorphic loaders by third-party MaaS and PPI service providers in the underground markets, and also pieces of controversial, potentially North-Korean-linked PseudoManuscript code.
You can simply block, by default, all access to all uncategorized sites. But wielding such a blunt policy instrument is likely to introduce a range of problems for users trying to access legitimate sites, and negatively affect business velocity.
BlackGuard, which was first spotted in March 2022, has experienced an upgrade with several new capabilities. It added a crypto wallet hijacker module that has hardcoded addresses and support for multiple cryptocurrencies. The stealer can now propagate via USB and other removable devices to infect new hosts. Also, it can now steal data and drain […]
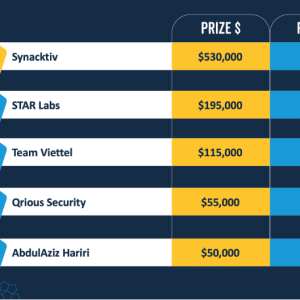
On the third day, contestants were awarded $185,000 after demonstrating 5 zero-day exploits targeting the Ubuntu Desktop, Windows 11, and the VMware Workstation software.
Parts of Twitter’s source code were recently leaked online via GitHub, the New York Times reports, but were taken down after the social media platform filed a DMCA request.