A spokesperson for Latvia’s Ministry of Defense confirmed that the latest attack was “most likely” linked to Russia’s Gamaredon, although the investigation is still ongoing.
Organizations are optimistic about the security of open-source software development, with an average of 77% believing the security of open-source development will improve by the end of 2023, according to a 2022 Linux Foundation report.
The threat actor known as Cobalt Sapling was spotted targeting Saudi Arabia by creating a new sub-group dubbed Abraham’s Ax. Researchers also found a connection between Moses Staff and Abraham’s Ax. Both rely on the same custom cryptographic wiper malware for encrypting the victim’s data. To stay protected, experts recommend organizations audit the access controls […]
More than two years later, Hackney Council is still dealing with the colossal aftermath of a ransomware attack. While its services are now back up and running, parts of the council are still not operating as they were prior to the attack.
A specialist music academy in Guildford, southwest of London, has confirmed that a cyberattack is responsible for knocking out its phone lines and impacting the school’s IT systems.
The company says the breach stems from a system containing customer data “relating to some online orders placed between November 2018 and October 2020” and that customers are at risk from scammers.
As part of the investment, ABN AMRO will integrate Hadrian technology into its platform. The company stated it has formed tens of thousands of digital endpoints as it has grown its digital infrastructure over the years.
Despite not being the true LockBit Locker group, these micro criminals were still able to cause significant damage by encrypting a large number of internal files at SMBs in Belgium.
Security researcher Gtm Manoz from Nepal discovered in September 2022 that a system designed by Meta for confirming a phone number and email address did not have any rate-limiting protection.
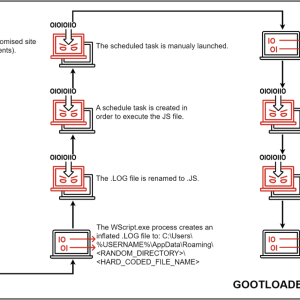
Gootkit runs on an access-a-as-a-service model used by different groups to drop additional malicious payloads on compromised systems. It has been known to use fileless techniques to deliver threats such as SunCrypt, REvil, Kronos, and Cobalt Strike.