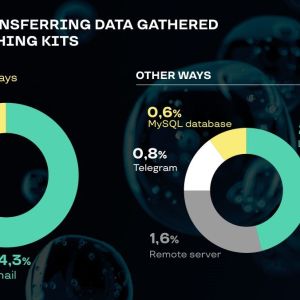
Cybercriminals often use legitimate services such as Google Forms and Telegram to obtain user data stolen on phishing websites to help keep it safe and start using the information immediately.
Researchers from Claroty have found and privately disclosed nine vulnerabilities affecting Rockwell Automation’s FactoryTalk AssetCentre, an ICS-specific backup solution.
This supply chain attack took place around April 1, 2021, the ad-injecting malware was delivered to the Android devices of the Germany-based communications technology vendor.
Ryuk was among the first high-touch “human-operated” ransomware campaigns that have become prevalent in recent years, affecting both public and private sector organizations with crippling attacks.
The appeal of disruptive technologies is that they offer clearly improved ways of doing things. But it also means facing new openings for threat actors, which brings the CISO role into focus.
The malicious document targets the government of Azerbaijan using a SOCAR letter template as a phishing lure. SOCAR is the name of Azerbaijan’s Republic Oil and Gas Company.
Cybersecurity weaknesses persist throughout the U.S. DOE’s unclassified networks, including those of the National Nuclear Security Administration, according to an inspector general audit.
The seller did not disclose how they got the cache but claimed that it included 895,000 gift cards from 3,010 companies, including Airbnb, Amazon, American Airlines, Nike, Subway, Target, and Walmart.
Google announced that the Android Open Source Project (AOSP) now supports the Rust programming language for developing the OS itself to prevent memory safety vulnerabilities.
The leaked files contain information of the LinkedIn users whose data has been allegedly scraped, including their full names, email addresses, phone numbers, workplace information, and more.