Members will include representatives of tech companies, critical infrastructure entities, academia, and government agencies, as well as “leaders in the civil rights, civil liberties, and privacy communities,” DHS Secretary Alejandro Mayorkas said.
A controversial executive order that would require U.S. cloud companies to closely monitor the identities of their customers will move one step closer to the finish line next week amid opposition from the industry.
The tool allows users to directly recover multiple types of credentials from the LSASS without accessing its memory. This includes recovering Kerberos tickets, SSO cookies, DPAPI credential keys, and NTLMv1 responses.
The attacks recently observed by Okta route requests through anonymizing services like TOR and residential proxies such as NSOCKS, Luminati, and DataImpulse. The experts noticed that millions of requests have been routed through these services.
A Bitwarden survey showed that 25% of respondents globally reuse passwords across 11-20+ accounts, and 36% admit to using personal information in their credentials publicly accessible on social media (60%) platforms and online forums (30%).
The cards are labeled “Virus Trojan Horse Removal Payment Card” and “Unpaid Bill Late Fee Payment Card,” and were created by the Echizen Police in the Fukui prefecture in Japan as an alert mechanism.
Nearly five months after security researchers warned of the Cactus ransomware group leveraging a set of three vulnerabilities in Qlik Sense data analytics and BI platform, many organizations remain dangerously vulnerable to the threat.
The FBI published a warning on Friday about the scam, noting that it was akin to an offshoot of romance scams and pig butchering schemes that have proliferated in recent years.
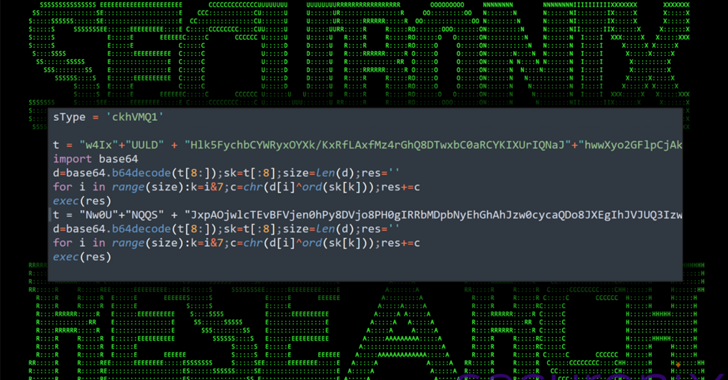
An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor.
The operation involves a malicious PPSX file that drops a custom loader for the Cobalt Strike Beacon malware. The loader employs various techniques to slow down analysis and bypass security solutions.