A Utah company exposed the information of more than 50,000 customers by storing data on an unsecured server. Sensitive customer data stored in a publicly accessible database included scans of passports and health insurance ID cards among others.
Threat actors have started to use ‘Promoted’ tweets, otherwise known as Twitter ads, to spread cryptocurrency giveaway scams. These scams have been successful for the threat actors, with one round of scams generating over $580,000 in a single week.
Google has fixed a second actively exploited Chrome zero-day this month with the release of Chrome 89.0.4389.90 to the Stable desktop channel for Windows, Mac, and Linux users.
The latest funding round was led by Felicis Ventures, with participation from HubSpot, Okta, Next47 (venture firm backed by Siemens), Basis Set Ventures, Operator Collective, and previous investors.
The Chicago-based company said in a regulatory filing that the hack has taken its systems offline, delaying and disrupting parts of Molson Coors’ operations, including its production and shipments.
To pressurize its victims for paying up the ransom quickly, REvil gang has started launching DDoS attacks and calling victims’ business partners and journalists in an attempt to publicize the breach news.
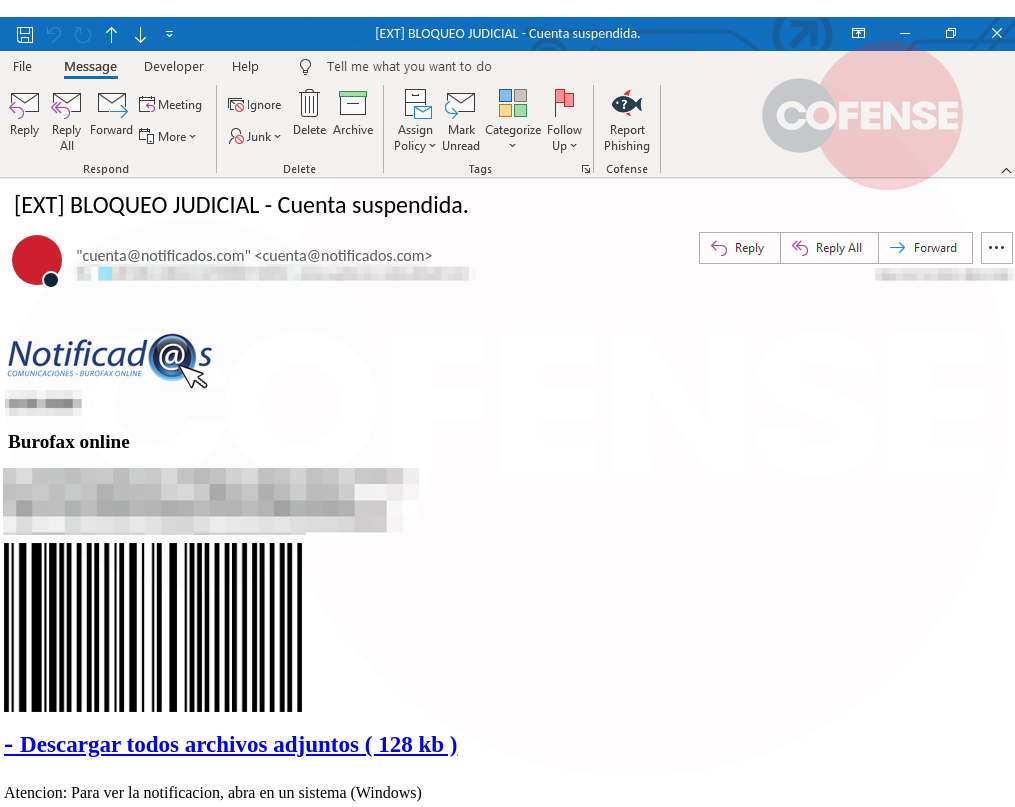
The Cofense Phishing Defense Center (PDC) has observed Latin American banking Trojans abusing AutoHotKey (AHK) and the AHK compiler to evade detection and steal users’ information.
A new feature added to the abilities of TrickBot can allow attackers to check devices for well-known vulnerabilities that can be exploited to read, write, or erase the UEFI/BIOS firmware.
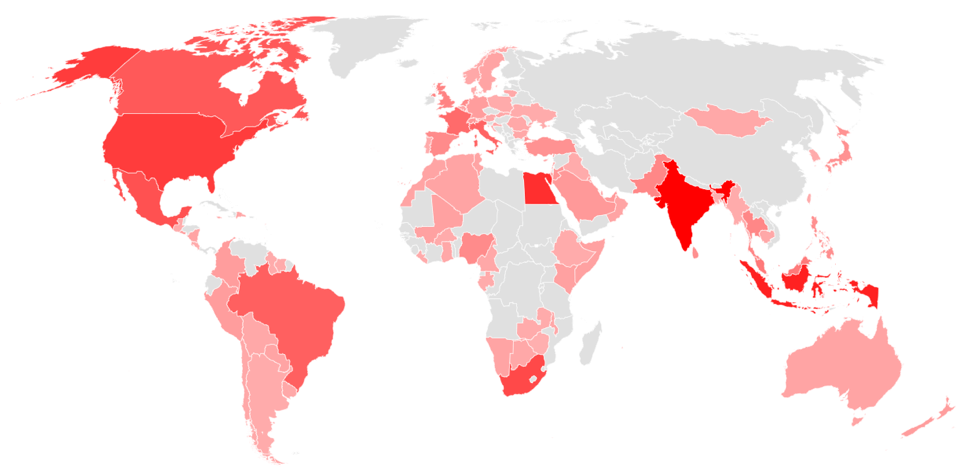
This month, Trickbot ranks as most popular malware impacting 3% of organizations globally, closely followed by XMRig and Qbot which also impacted 3% of organizations worldwide respectively.
The investigation led to the discovery of a new group called “Netbounce” and it exposed their malware delivery infrastructure. What made this stand out is their unique set of tools and techniques.