Someone has set up a website named SolarLeaks where they are offering to sell gigabytes of files allegedly obtained as a result of the recently disclosed SolarWinds breach.
Cybersecurity researchers took the wraps off an ongoing surveillance campaign directed against Colombian government institutions and private companies in the energy and metallurgical industries.
When exploited, this vulnerability can be triggered by a single-line command to instantly corrupt an NTFS-formatted hard drive, with Windows prompting the user to restart their computer to repair the corrupted disk records.
The US Cybersecurity and Infrastructure Security Agency (CISA) said today that threat actors bypassed multi-factor authentication (MFA) authentication protocols to compromise cloud service accounts.
Treasury’s Office of Foreign Assets Control identified the firm, Barkat Ventures, as an arm of an organization that the supreme leader of Iran controls called EIKO, short for Execution of Imam Khomeini’s Order.
Internet of Things devices are highly susceptible to attacks, breaches, and flaws emanating from issues within the TCP/IP network communications architecture. Here’s an overview of what you need to know to mitigate risks.
On the heels of a previously-reported cyberattack on the European Medicines Agency (EMA), cybercriminals have spilled compromised data related to COVID-19 vaccinations onto the internet.
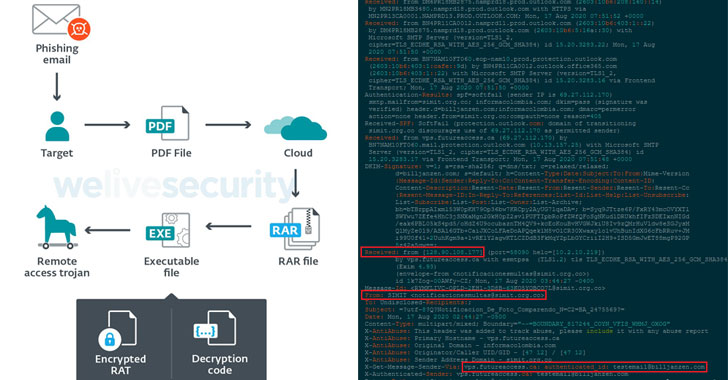
Dubbed Rogue, the Trojan is the work of Triangulum and HeXaGoN Dev, known Android malware authors that have been selling their malicious products on underground markets for several years.
A watchdog agency for the U.S. Census Bureau says that proper information-technology security safeguards weren’t in place leading up to the start of the 2020 census last year.
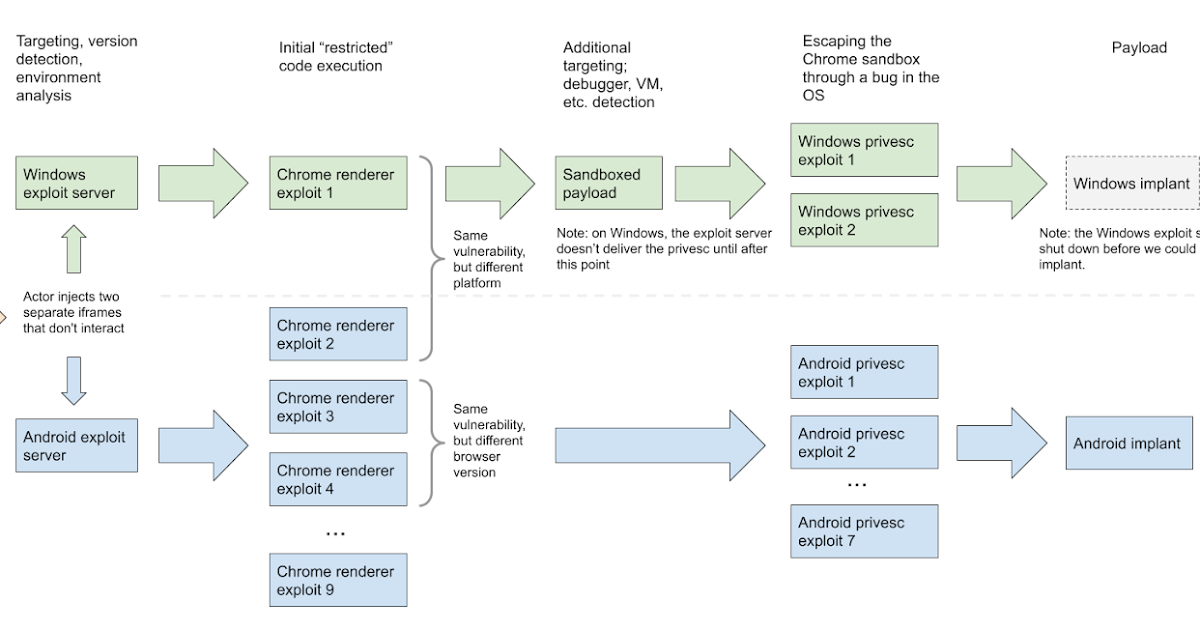
Researchers discovered two exploit servers delivering different exploit chains via watering hole attacks. One server targeted Windows users, the other targeted Android devices.