Those best practices would need to comply with recommendations from or protecting data from the National Institute of Standards and Technology or some other government-endorsed standards body.
The SolarWinds supply chain compromise won’t be the last of its kind. Vendors and enterprises alike must learn and refine their detection efforts to find the next such attack.
“We recently became aware of unauthorized access to certain of our information technology systems hosted by a third party cloud provider,” Ubiquiti said in emails sent to customers today.
The Pentagon has six months to release a full report on what they know about the existence of Unidentified Aerial Phenomena (UAP) — or UFOs to the rest of us. This creates room for new phishing scams.
Colorado-based short line rail operator and logistics provider OmniTRAX was hit by a recent ransomware attack and data theft that targeted its corporate parent, Broe Group.
Enterprise use of biometrics for security may see an uptick by organizations looking to defend themselves from attacks, but they must weigh the concerns against the benefits.
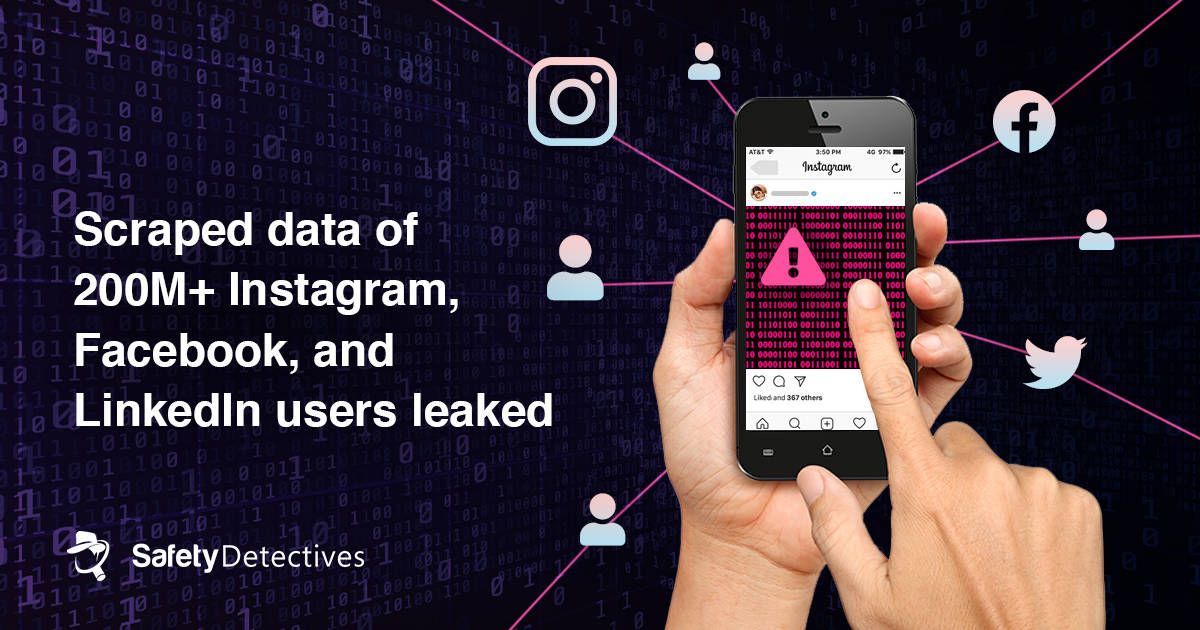
The company’s unsecured ElasticSearch database contained personally identifiable information (PII) from at least 214 million people from around the world using Facebook, Instagram, and LinkedIn.
The number of U.S. federal agencies confirmed to have been breached in a suspected Russian espionage campaign will likely increase as the investigation continues, the head of the CISA said.
The actor used the BumbleBee webshell to upload and download files to and from the compromised Exchange server, but more importantly, to move laterally to other servers on the network.
Cybersecurity as an industry must also look to harness the power of storytelling and so that it can become more relatable for the audience and make the subject matter easier to understand.