Microsoft was impersonated in 38% of all brand phishing attacks in Q1 2024, according to new data from Check Point. Google was the second most impersonated brand in Q1 2024, making up 11% of attempts.
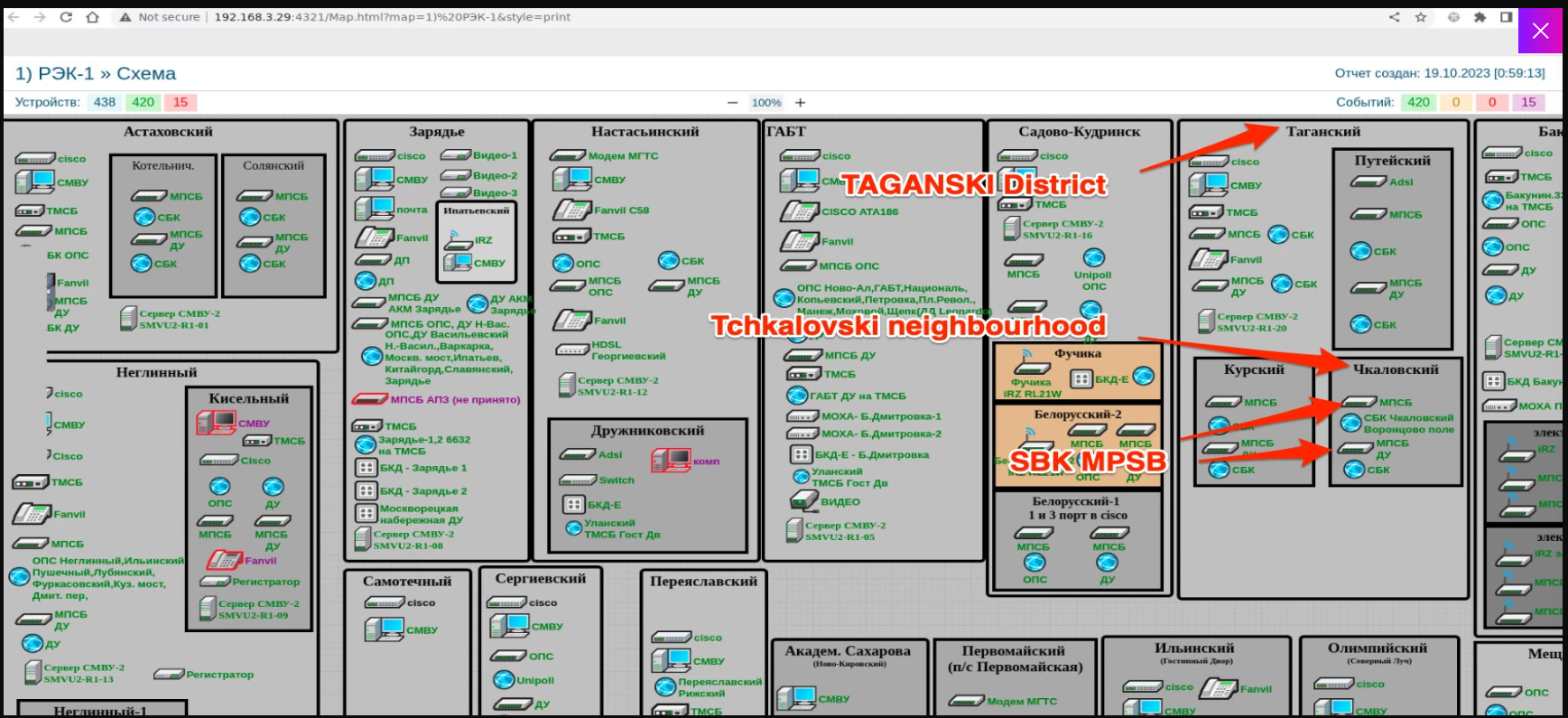
The attack chain sees hackers targeting a list of sensor gateways IPs. Threat actors distributed their malware to each target, likely either through remote-access protocols such as SSH or the sensor protocol (SBK) over port 4321.
Orrick Herrington & Sutcliffe’s proposed agreement with plaintiffs, filed last week in a northern California federal court, settles four proposed consolidated class action lawsuits filed against it in the wake of the March 2023 hacking incident.
The attacks begin with malicious emails containing seemingly innocuous document attachments (Excel and Word files) that exploit the CVE-2017-11882 flaw, a commonly targeted Microsoft Office Equation Editor vulnerability fixed in 2017.
This maximum severity security flaw (CVE-2024-3400) affects PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewalls with device telemetry and GlobalProtect (gateway or portal) enabled.
At many financial institutions, your voice is your password. Tiny variations in pitch, tone and timbre make human voices unique – apparently making them an ideal method for authenticating customers phoning for service.
The threat actor known as Muddled Libra has been observed actively targeting software-as-a-service (SaaS) applications and cloud service provider (CSP) environments in a bid to exfiltrate sensitive data.
A secretive U.S. cyber military force ramped up global operations in 2023, executing more than double the average number of “hunt forward” campaigns than the previous five years, according to the head of U.S. Cyber Command.
Cybersecurity researchers have discovered a “renewed” cyber espionage campaign targeting users in South Asia with the aim of delivering an Apple iOS spyware implant called LightSpy.
Global cybersecurity services provider Cyderes has acquired Ipseity Security, a Canadian company specializing in identity and access management (IAM). The financial terms of the deal were not disclosed.