The malware injects JavaScript to perform unwanted redirects by using sophisticated obfuscation techniques, including time-based randomization and XOR encoding, to evade detection.
Worryingly, the social engineering scammers are likely operating with little more than a cheap email list of self-employed US residents, according to the latest advisory from Malwarebytes Labs.
Curious Serpens has been active since at least 2013. This threat actor is associated with espionage and has targeted organizations in the Middle East, the United States, and Europe.
These attachments, as per Microsoft Threat Intelligence’s blog post, contain malware that steals your login credentials, or they might redirect you to a fake website that looks like a legitimate tax platform designed to capture your information.
The vulnerability allows unauthenticated attackers to expose assets in the environment, with a high impact on confidentiality, integrity, and availability, without requiring user interaction.
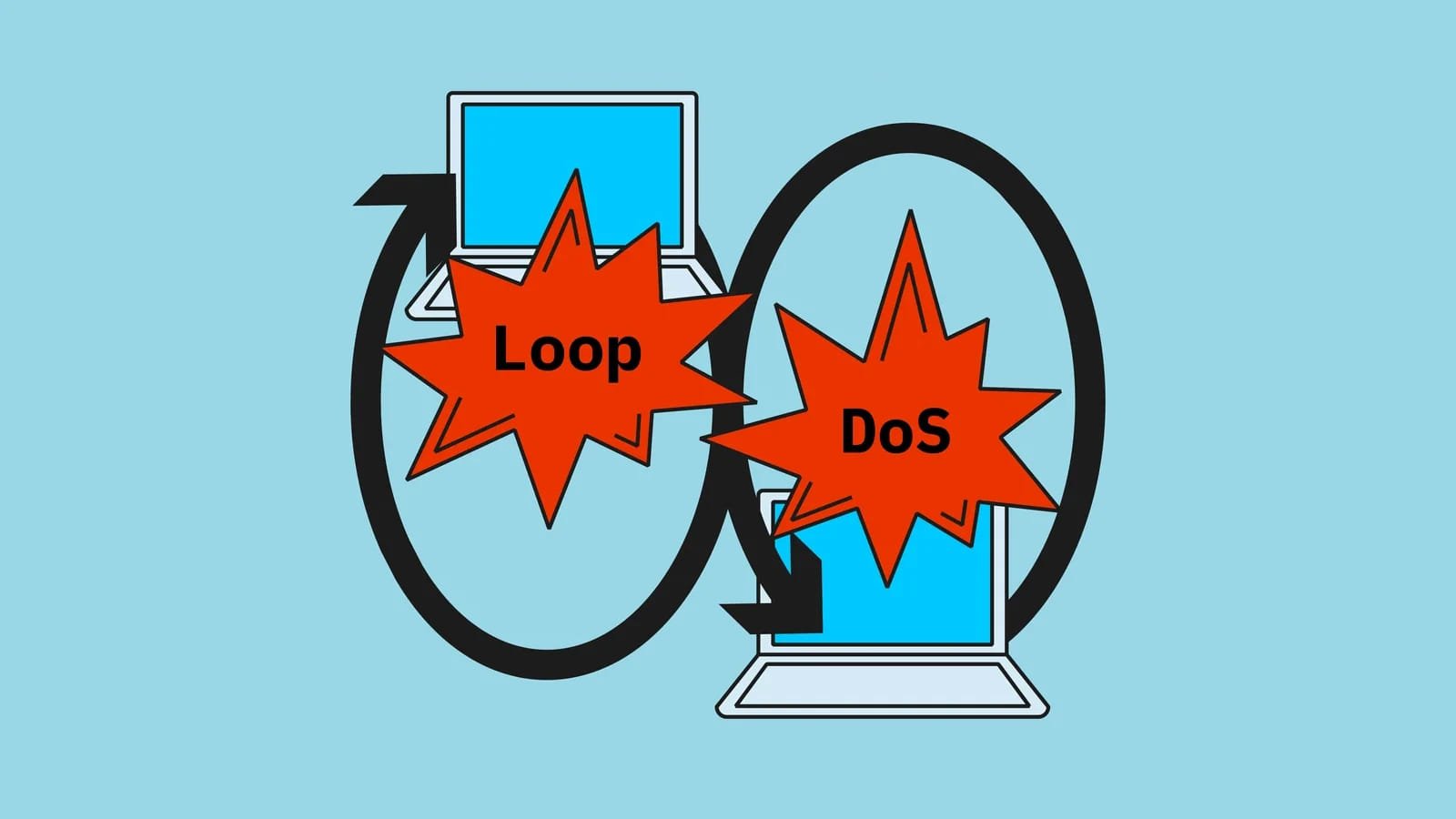
Devised by researchers at the CISPA Helmholtz-Center for Information Security, the attack uses the User Datagram Protocol (UDP) and impacts an estimated 300,000 host and their networks.
An analysis of 100,000+ Windows malware samples has revealed the most prevalent techniques used by malware developers to successfully evade defenses, escalate privileges, execute the malware, and assure its persistence.
New research has shed light on the profound impact of ransomware attacks on the IT and construction sectors, revealing that these industries bore the brunt of nearly half of all incidents in 2023.
While the language businesses use in Item 1.05 filings are ultimately crafted to notify regulators and investors of potential risks, these words also signal how a company detects, mitigates, contains, and recovers from cyberattacks.
Lynis is a comprehensive open-source security auditing tool for UNIX-based systems, including Linux, macOS, and BSD. Its main objective is to evaluate security measures and recommend enhancing system hardening.