SolarWinds has disclosed two vulnerabilities in their Access Rights Manager (ARM) software: CVE-2024-28990 (CVSS 6. 3) allows for a hardcoded credential authentication bypass, while CVE-2024-28991 (CVSS 9. 0) enables remote code execution.
The Lazarus Group has been targeting developers in a new VMConnect campaign, using fake job interviews to trick them into downloading malicious software packages from open-source repositories.
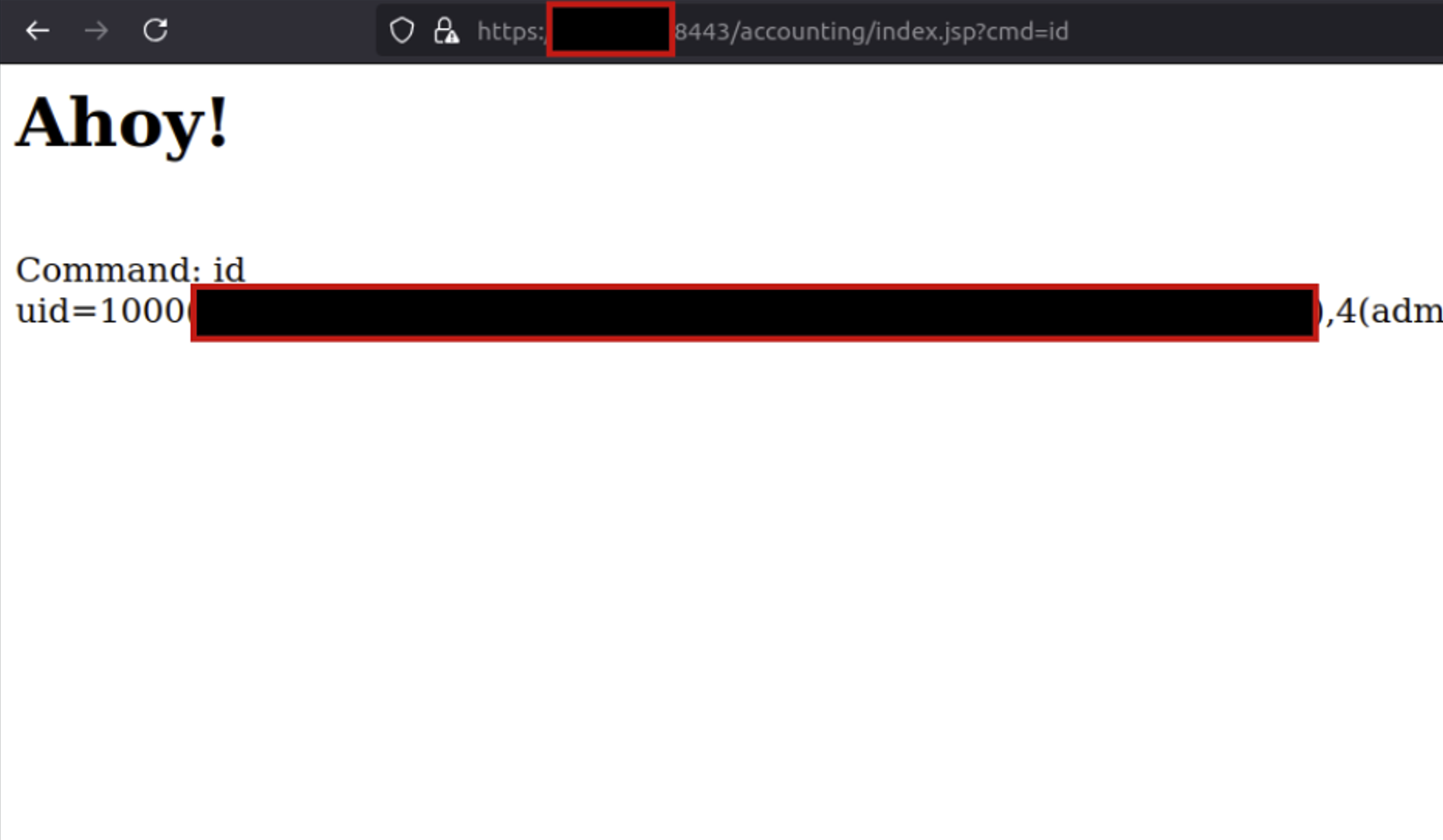
Hackers are targeting an RCE vulnerability (CVE-2024-45195) in Apache OFBiz after the release of a Proof of Concept (PoC) exploit. Malicious requests have been detected, with attacks focusing on the financial services industry and business sectors.
By exploiting web app services, the attackers deploy a web shell to launch malware and gather credentials, compromising IIS servers to spread the BadIIS malware. The malware facilitates proxy ware and SEO fraud by manipulating search engine rankings.
Two critical remote code execution (RCE) flaws, identified as CVE-2024-8695 and CVE-2024-8696, have been uncovered in Docker Desktop, a popular tool for containerized application development.
The group deployed sophisticated malware named Veaty and Spearal against Iraqi targets, using distinctive command and control mechanisms, including a custom email-based channel identified within the Veaty malware.
Adobe has completed a fix for a critical bug in Reader with a known Proof of Concept (PoC) exploit for CVE-2024-41869. The update also addresses another critical flaw, CVE-2024-45112, in various versions of Acrobat and Reader.
A new Linux malware named Hadooken is targeting Oracle WebLogic servers, dropping Tsunami malware and deploying a cryptominer. WebLogic servers are vulnerable to cyberattacks due to flaws like deserialization and weak access controls.
According to ISC2, the global cybersecurity workforce growth has stagnated at 5. 5 million professionals, increasing by just 0. 1% in a year, marking the sector’s first stall since 2019.
Created to combat data leaks within publicly available Docker images, DockerSpy automates the process of scanning for secrets to enhance security and compliance. Its scanning engine can identify various secret types and provides detailed analysis.