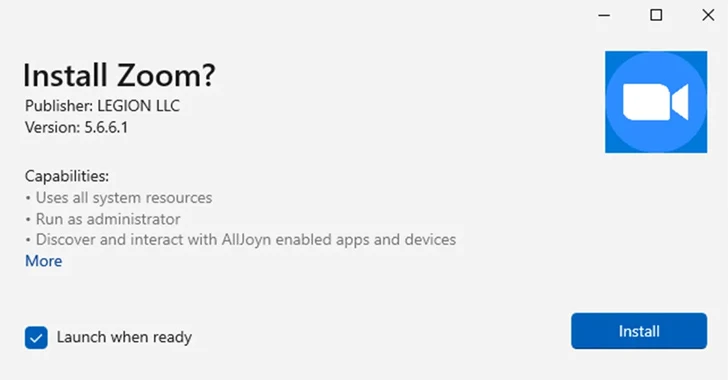
Multiple financially motivated hacking groups have been observed using the App Installer service as an entry point for ransomware attacks, leveraging signed malicious MSIX app packages distributed via Microsoft Teams and malicious search engine ads.
Experts caution that the decision to pay or not pay depends on various factors, including the type of data compromised, the availability of backups, the financial impact on the organization, and the sector in which the company operates.
The August data breach at Kroll exposed personal information of FTX bankruptcy claimants, including coin holdings and balances, making them potential targets for threat actors in the cryptocurrency market.
The malware is sold as a service and can be obtained through malvertising, fake browser updates, and cracked software installations. It has also been found that the malware is being spread through Discord’s content delivery network.
The National Insurance Board in Trinidad and Tobago has been hit by a ransomware attack, leading to the closure of its offices and limiting its operations for an extended period.
The attack occurred on December 24, 2023, and caused severe disruptions to the hospitals’ IT systems. Investigations are underway to determine the extent of the damage and whether any data was stolen.
The Albanian parliament and a telecom company were targeted by cyberattacks originating from outside Albania. The attacks, which attempted to interfere with infrastructure and delete data, have not been attributed to a specific threat actor.
The newly surfaced DragonForce ransomware gang has claimed responsibility for the attack, stating that they have encrypted devices and stolen data, including personal information of Ohio Lottery customers and employees.
The secret hardware function targeted by the attackers allowed them to bypass advanced memory protections, enabling post-exploitation techniques and compromising system integrity.
SE Labs has warned that multi-factor authentication (MFA) is not foolproof and can be bypassed by attackers using old-school methods such as social engineering, malware, and phishing.