Johnson Controls has released patches for a critical vulnerability found in some of its industrial refrigeration products. The flaw, known as CVE-2023-4804, could allow unauthorized access to debug features.
The funding opportunity includes investments in technologies, tools, training, and processes to strengthen cybersecurity, as well as increasing access to technical assistance and training for organizations with limited resources.
FortiGuard Labs has identified a Russian-language Word document with a malicious macro in the ongoing Konni campaign. The campaign uses a remote access trojan (RAT) to gain control of infected systems.
Along with others, Joseph Garrison stole approximately $600,000 from 1,600 victim accounts by adding a new payment method, depositing $5 into each account, and then withdrawing the funds.
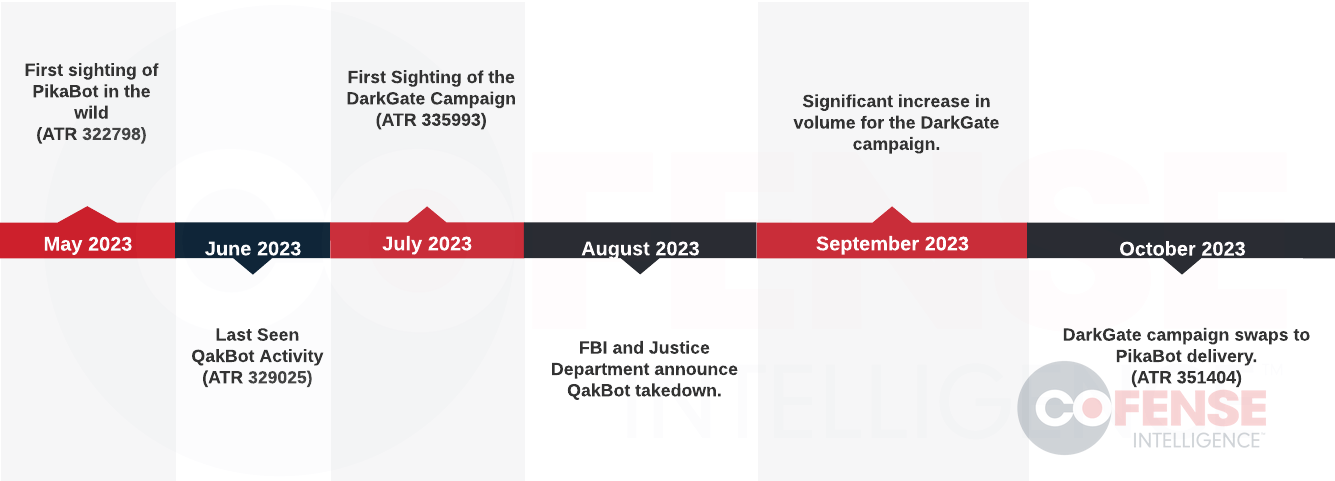
Phishing campaigns are using tactics previously seen in attacks involving the QakBot trojan to deliver malware families such as DarkGate and PikaBot. These campaigns utilize hijacked email threads, unique URL patterns, and a similar infection chain.
The majority of state-sponsored cyberattacks against Russia are believed to originate from North Korea and China, according to a report by Russian cybersecurity firm Solar. This comes as a surprise given the political partnerships between them.
The ICO believes Clearview’s mass scraping of personal information infringes on the data rights of U.K. residents and seeks to overturn the court’s decision to protect their privacy.
The FCC’s proposal comes in response to demands from lawmakers, E-Rate applicants, and school connectivity advocates to address the urgent need for cybersecurity protections in schools and libraries.
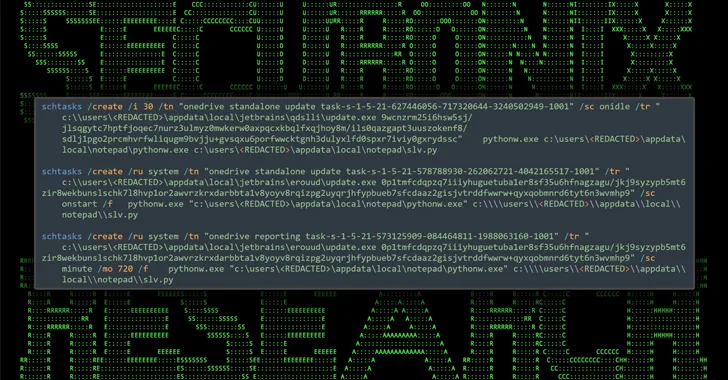
The ultimate goal of the attack is to deceive users into downloading a fake WinSCP installer that contains malware, while also establishing persistence and contact with a remote server.
The attackers posed as a group soliciting donations for children in Palestine, using emotionally charged language and news articles to manipulate recipients. They requested cryptocurrency donations and employed tactics to conceal their identity.