The company revealed on Tuesday that a “potential security incident” discovered on November 3 involved unauthorized access to a Sumo Logic AWS account through the use of compromised credentials.
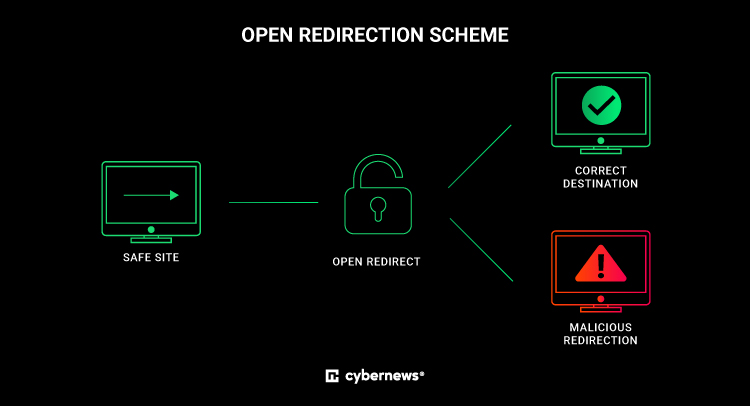
“The vulnerability can be exploited by attackers to trick users into visiting malicious websites or phishing pages by disguising the malicious URL as a legitimate one,” Cybernews researchers explained.
The malware runs a Discord bot and enables the threat actor to harvest a wide range of information, including passwords from web browsers and screenshots, execute arbitrary commands, encrypt files, and deactivate Microsoft Defender on the host.
By monitoring telemetry associated with two prominent Chinese APT groups, researchers observed network connections predominately originating from Cambodia, including inbound connections originating from at least 24 Cambodian government organizations.
On Monday evening, the maker of electronics and aerospace products replaced its website with a static message indicating some of its servers were accessed by hackers last Thursday.
The contents of the leaked database on BreachForums, as observed by Hackread.com, include publicly available information from LinkedIn profiles, containing full names and profile bios.
Farnetwork has been linked to the development and management of various ransomware strains, including JSWORM, Nefilim, Karma, Nemty, and their own program based on the Nokoyawa ransomware.
The hackers responsible for the attack, known as the DAIXIN Team, have gradually leaked samples of the stolen patient data and expressed interest in selling it to data brokers.
According to a statement published by the resort, the incident occurred on October 19-20 and involved unauthorized third-party access to its non-casino customers’ loyalty program membership data.
This attack on the flour plant is part of a series of cyber attacks by the group on Israeli organizations, including a successful attack on the Ashalim Power Station and taking control of military servers and systems.