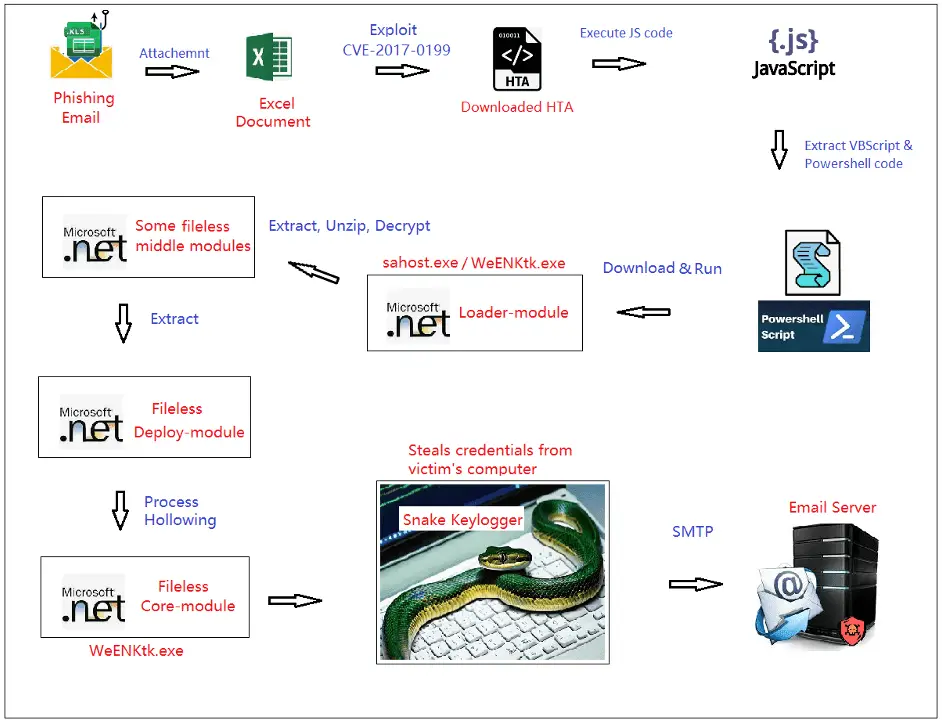
The attack starts with a phishing email disguised as a fund transfer notification, with an attached Excel file named “swift copy.xls” that triggers the deployment of Snake Keylogger on the victim’s computer upon opening.
The ransomware operation focuses on data theft extortion rather than encrypting files, with victims facing the threat of stolen data being leaked or sold if negotiations fail.
The QiAnXin Threat Intelligence Center has revealed the details of “Operation DevilTiger,” a cyber espionage campaign carried out by the elusive APT-Q-12 group, also known as “Pseudo Hunter.”
The campaign, which targeted organizations worldwide, involved impersonating tax authorities from various countries and utilizing Google Sheets for command and control (C2).
The Godzilla fileless backdoor relies on a complex series of actions, such as cryptographic operations, class loading, and dynamic injection, to establish unauthorized access.
The U.S. Department of State and the Secret Service are offering a reward of $2.5 million for information leading to the capture of Belarusian cybercriminal Volodymyr Kadariya, who is linked to the Angler Exploit Kit.
Cequence Security found that cyberattacks against the travel industry surge during holidays, with 91% of severe vulnerabilities in the top 10 travel and hospitality sites enabling man-in-the-middle attacks.
U.S. cybersecurity leaders are focusing on preparing for the potential risks posed by quantum cryptography tools that could threaten critical infrastructure and national security.
The FBI investigation revealed that the suspect, Daniel Rhyne, had accessed the company’s systems without authorization and changed passwords for various accounts. Rhyne’s actions were intended to deny the company access to its systems and data.
Third-party risk management is a critical issue in the wake of the CrowdStrike IT outage, revealing vulnerabilities within financial institutions related to supply chain resilience, especially in vital sectors like financial services.