The recently discovered malicious Python packages, such as tablediter, request-plus, and requestspro, are believed to be a continuation of the VMConnect campaign attributed to North Korean threat actors.
The network hardware giant Netgear has discovered two vulnerabilities affecting one of its router models and its network management software. One of the flaws, tracked as CVE-2023-41183, allows hackers to exploit Netgear’s Orbi 760 routers.
Forever 21 experienced a data breach that compromised the personal information, including names and Social Security numbers, of over 539,000 individuals. The breach occurred between January 5, 2023, and March 21, 2023.
Hyperproof, a software-as-a-service risk and compliance management company, today announced that it raised $40 million in a funding round led by Riverwood Capital, with participation from Toba Capital, an early-stage VC firm.
The National Safety Council has leaked nearly 10,000 emails and passwords of their members, exposing 2000 companies, including governmental organizations and big corporations.
To effectively safeguard against the risks of IoT sprawl, continuous monitoring, and absolute control are crucial. However, that requires accurate identification of all IoT devices and operating systems (OSes) within the enterprise network.
Earth Estries uses advanced techniques such as DLL sideloading and has developed three custom malware tools: Zingdoor, TrillClient, and HemiGate. It has been active since at least 2020 and has similarities with another group called FamousSparrow.
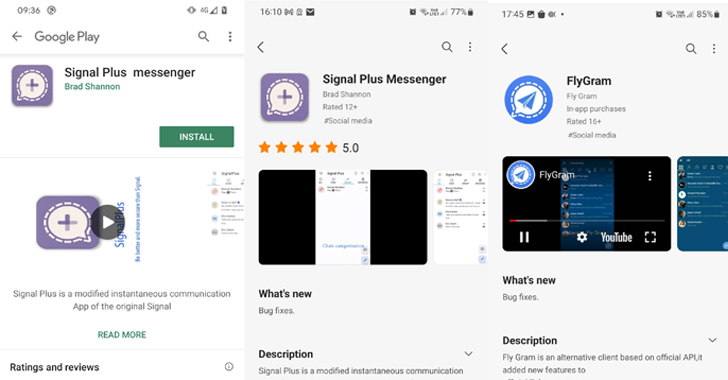
Cybersecurity researchers have discovered malicious Android apps for Signal and Telegram distributed via the Google Play Store and Samsung Galaxy Store that are engineered to deliver the BadBazaar spyware on infected devices.
Now, teams using GitHub Actions can also create their own custom deployment protection rules, to ensure that only “the deployments that pass all quality, security, and manual approval requirements make it to production,” GitHub explained.
An unknown threat actor is leveraging malicious npm packages to target developers with an aim to steal source code and configuration files from victim machines, a sign of how threats lurk consistently in open-source repositories.