A key reason it was so tricky for researchers to identify TZW as a spinoff of Adhubllka is because of the small ransom demands the group typically makes. At such a level, victims often pay attackers and the attackers continue to fly under the radar.
On August 14 and 15, the cybercriminals leaked nearly 1 Tb of information allegedly stolen from 16 of the victims, Resecurity said. These victims include UCLA, Siemens Energy, Cognizant, and cybersecurity firms Norton LifeLock and Netscout.
The good news is that the scam is an empty threat that aims to play on the victim’s fear of leaking data. By knowing this, they can then be confidently ignored. ESET traced one scam wherein an actor demanded £1000 ($1260) in BTC from the victim.
A revised data breach notification is being sent to victims stating that attackers may have also stolen their credit/debit card number, beyond the raft of personal information.
The activities observed suggest the threat actor intends to perform espionage and maintain access to organizations across a broad range of industries for as long as possible.
In H1 2023, compromised credentials accounted for 50% of root causes, whereas exploiting a bug came in at 23%. We can’t conclusively say that attackers are favoring compromised credentials over vulnerabilities, but it can’t be denied either.
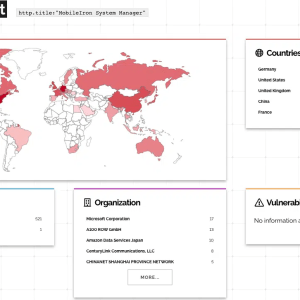
The vulnerability could be exploited to access sensitive API data and configurations, run system commands, or write files onto the system. The vulnerability CVE-2023-38035 impacts Sentry versions 9.18 and prior.
Malicious actors are targeting Roblox developers with a new malware called Luna Grabber, distributed through npm packages that impersonate legitimate software. These fake packages, including noblox.js-vps, noblox.js-ssh, and noblox.js-secure, house malicious multi-stage payloads. This campaign underscores the recurring strategy of threat actors employing typosquatting as a tactic to deceive developers.
In a public statement published on August 23, 2023, Pôle emploi confirmed “a breach in the information system of one of its service providers, involving a risk of disclosure of jobseekers’ personal data.”
Despite the shutdown of certain internal systems following the detection of unusual network activity, SRHS disclosed that workarounds have been implemented to ensure the partial continuation of business operations.