The 2nd Judicial Circuit announced Monday that law enforcement is investigating a data breach involving Gadsden County court records. In a news release, the circuit said that initial assessments show some of the records contained PII.
There’s mounting evidence that Akira ransomware targets Cisco VPN (virtual private network) products as an attack vector to breach corporate networks, steal, and eventually encrypt data.
The group claims to have stolen military contracts, internal call signs, and personal data, amounting to 1.6 TB. If the attack gets confirmed, the disclosure of confidential information poses a serious risk to organizations involved in the contracts.
The group appears to be skilled and patient, selectively pushing payloads to specific victims. The use of signed malware and supply chain attacks makes it difficult for security software to detect.
The investment brings Grip Security’s total funding to $66 million and marks a major milestone for the company, further accelerating its go-to-market strategy and advancing product development.
Ukrainian hackers claim to have broken into the email account of a senior Russian politician and exposed documents that allegedly prove his involvement in money laundering and sanction evasion schemes.
The investment round was led by Two Sigma Ventures, with additional funding from Outpost Ventures, AV8, Bowery Capital, Founders Fund, Incubate Fund, Okta Ventures, Ridge Ventures, Salesforce Ventures, and Tau Ventures.
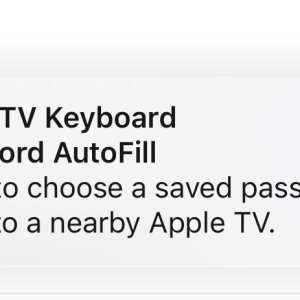
The spoofed Apple device prompts users to connect their Apple ID or share a password with a nearby Apple TV, allowing threat actors to collect data such as phone numbers and Apple ID emails.
Seiko apologized to the potentially impacted customers and business partners and urged them to be vigilant against email or other communication attempts potentially impersonating Seiko.
The HiatusRAT malware group reemerged to target Taiwan-based organizations and a U.S. military procurement system allegedly to snoop on military contracts. The audacity of threat actors is evident in their disregard for previous disclosures and their minimal efforts to change their payload servers. The IOCs from this campaign are available for organizations to proactively take […]