Logpoint, a SIEM company based in Copenhagen, acquired Muninn, an AI-powered NDR startup, to enhance threat detection capabilities. Muninn’s AI technology is designed to detect complex attacks in environments where traditional methods fall short.
The investigation strategy shared by JPCERT/CC covers Application, Security, System, and Setup logs, which can reveal traces left by ransomware attacks and help identify the attack vector
The CISA has alerted to four newly exploited vulnerabilities in its KEV catalog. The vulnerabilities include critical flaws in D-Link and DrayTek Vigor routers, Motion Spell GPAC, and SAP Commerce Cloud.
Platforms like Github, Discord, and YouTube are used to distribute compromised game cheats, which contain malware such as Skuld Stealer and Blank Grabber, known for stealing sensitive information.
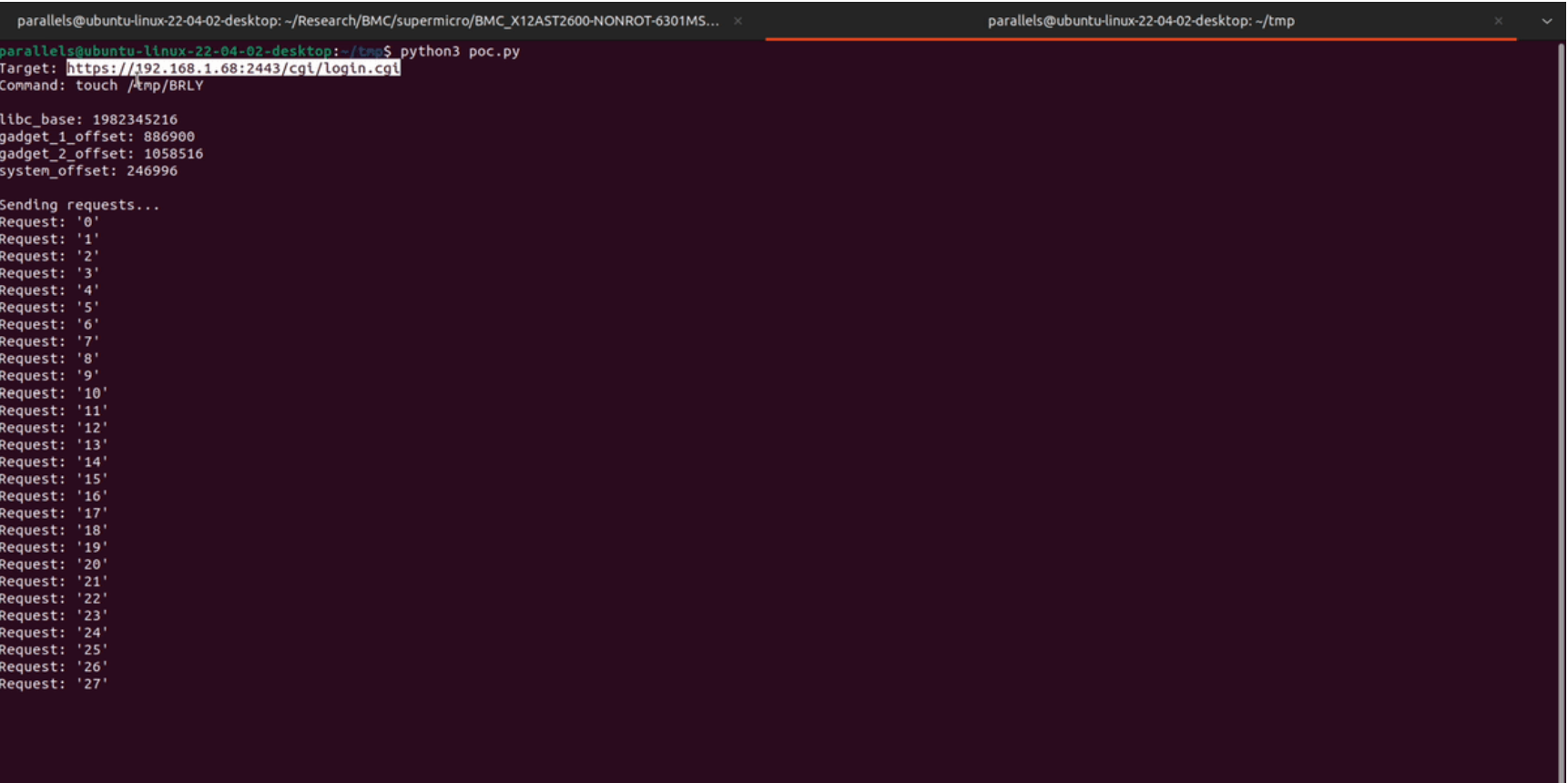
A critical vulnerability, CVE-2024-36435, has been found in several Supermicro enterprise products, allowing unauthenticated attackers to exploit a buffer overflow in the Baseboard Management Controller (BMC) firmware, leading to RCE.
Researcher Simone Margaritelli has uncovered a critical vulnerability that has been present in GNU/Linux systems for over a decade, scoring a 9.9 out of 10 for severity. This flaw allows attackers to gain complete control of vulnerable devices.
Meet three remarkable Danaher engineers who are excelling in their fields and paving the way for future generations of women in STEM.
Chemical engineering is cool, but it’s even cooler when making ice cream!
SWE is proud to award 328 scholarships, totaling nearly $1.5 million, to undergraduate and graduate engineering students for the 2024-2025 academic year. This year marks a special milestone as SWE celebrates 65 years of its scholarship program.
Catherine Hunt Ryan, president of Bechtel’s Manufacturing and Technology business, previews her WE24 keynote and discusses the pivotal role women play in infrastructure projects in this episode of Diverse: a SWE podcast.