The data includes granular details of pages viewed, buttons clicked and keywords searched. It is matched to the user’s IP address – an identifier linked to an individual or household – and, in many cases, details of their Facebook account.
FCEB agencies must patch or mitigate the vulnerability as ordered by the BOD 22-01 binding operational directive. However, this is no longer needed since Barracuda has already patched all vulnerable devices by applying two patches over the weekend.
Investigators found that the retailer was storing nearly 20 years’ worth of payment card data on its e-commerce server in plaintext format, protected by only a password, which the attacker guessed.
The QBot malware operation has started to abuse a DLL hijacking flaw in the Windows 10 WordPad program to infect computers, using the legitimate program to evade detection by security software.
A team of researchers at Georgia Tech, the University of Michigan, and Ruhr University Bochum developed this novel attack which can retrieve pixels from the content displayed in the target’s browser and infer the navigation history.
An updated version of the Python-based, cloud-focused hack tool called Legion—which can extract credentials from vulnerable web servers—has surfaced. The updated variant incorporates the Paramiko module to exploit SSH servers. Furthermore, it can now retrieve specific AWS credentials associated with CloudWatch, DynamoDB, and AWS Owl from Laravel web applications.
The Fort Lauderdale, Florida-based insurance company, said it detected unauthorized access to certain systems on March 6 and discovered that certain systems within the network were infected with malicious code.
Alleged Iranian nation-state hacker group Tortoiseshell performed a watering hole attack on several shipping and logistics websites in Israel to collect information about their users. Attackers stay hidden by impersonating the genuine jQuery JavaScript framework. Organizations are urged to raise awareness for watering hole attacks and always keep the systems updated.
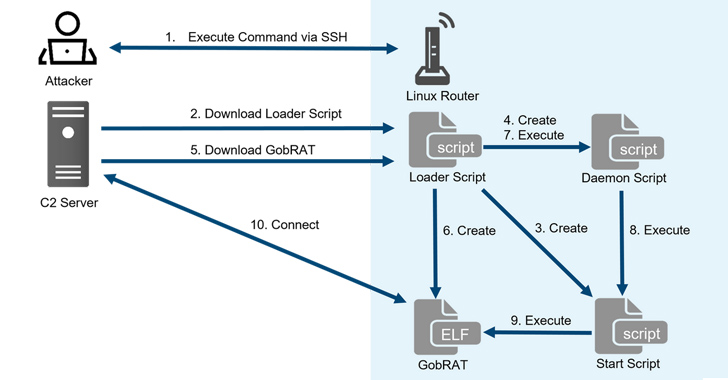
“Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT,” the JPCERT Coordination Center (JPCERT/CC) said in a report published today.
The AHA is urging federal regulators to back off from recent guidance that treats patient IP addresses as PHI, saying that the new rules would “reduce public access to credible health information” and create hardships for doctors and hospitals.