The Oklahoma Institute of Allergy Asthma and Immunology posted a notice on its doors this month saying it will be closing “effective immediately due to a cybersecurity event.” Clinics in the towns of Norman and Yukon were both closed.
The new way that hackers originate BEC 3.0 attacks is through legitimate services. In this attack, hackers create free Dropbox accounts and leverage their domain legitimacy to create pages with phishing embedded within them.
Ukraine’s top cybersecurity agency says Russian hackers took a sudden interest in obtaining personal data and mounted successful attacks against more than one-third of the country’s largest insurers.
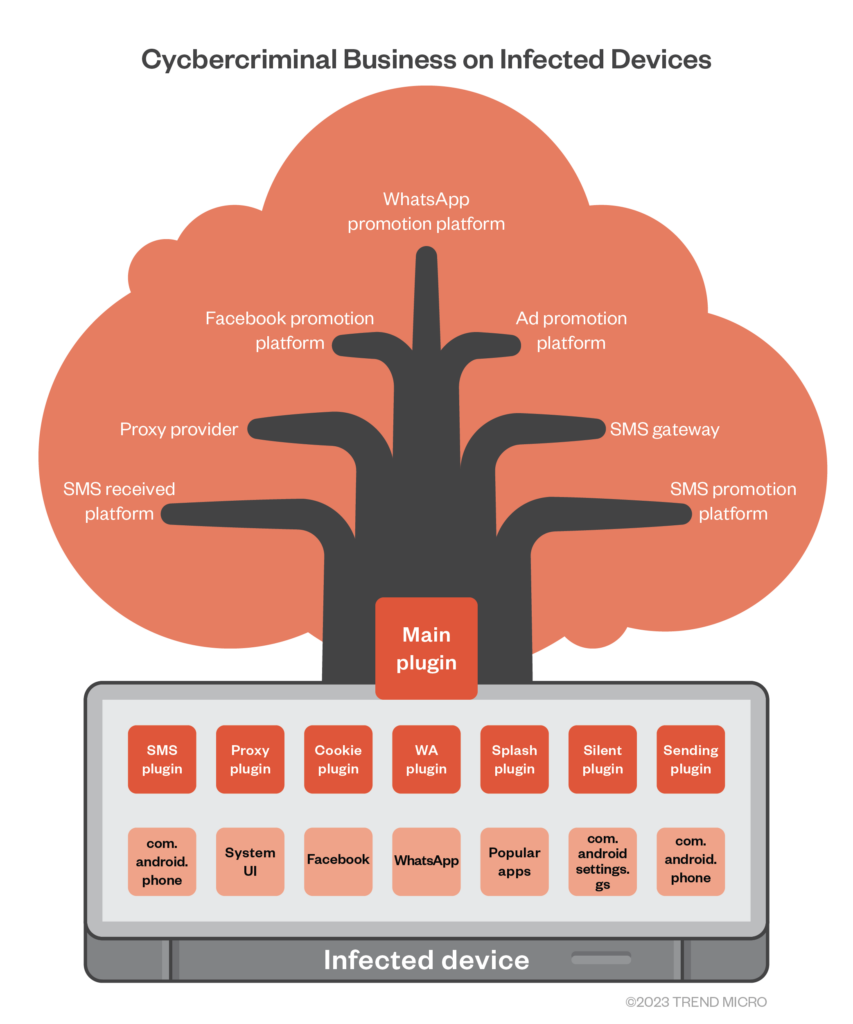
Since 2021, Trend Micro has been tracking a different operation that appears to be linked to Triada. The group behind the campaign is tracked by the cybersecurity firm as Lemon Group and the malware preloaded on devices is called Guerrilla.
The Royal ransomware group, which spun off from Conti in early 2022, is refining its downloader using tactics and techniques that appear to draw directly from other post-Conti groups, says Yelisey Bohuslavskiy, chief research officer at Red Sense.
The House Homeland Security Committee on Wednesday easily advanced legislation to ensure the federal government and critical infrastructure can tap open-source software securely.
Trellix has observed a surge in malicious emails targeted toward Taiwan, starting April 7 and continuing until April 10. The number of malicious emails during this time increased to over four times the usual amount.
Cyber-resilience has become a top priority for global organizations, but over half (52%) of those with programs are struggling because they lack a comprehensive assessment approach, according to Osterman Research.
According to Check Point, whose analysts discovered the malicious extensions and reported them to Microsoft, the malware enabled the threat actors to steal credentials, system information, and establish a remote shell on the victim’s machine.
Group-IB infiltrated the infrastructure of MichaelKors RaaS to divulge never-before-heard secrets of its affiliate nexus, which would often target critical sector entities. For instance, affiliates take back 80-85% of the ransomware payments. The common attack tactics used by MichaelKors include phishing emails having malicious links embedded in them.