Trend Micro noticed a ransomware variant called Rapture that adopts a minimalistic approach and leaves behind only a small digital footprint. The attackers utilized the commercial packer Themida to pack the ransomware, hence making the analysis challenging. An RSA key configuration file used by the attackers was found to be similar to that used by […]
Watch out for bugs in TP-Link, Apache Log4j2, and Oracle WebLogic Server that are under active exploitation by different cybercriminal groups, warns CISA. FCEB agencies are required to apply vendor-provided fixes by May 22, 2023.
Heimdal Security’s SOC team has discovered an ongoing phishing campaign that seems to be aimed at customers of Romanian telecom providers. The fraudulent page requests the victims to submit their credit card information to cover a tax related to changing a delivery address. Experts recommend avoiding opening suspicious emails or links, and using order tracking […]
Cyble has recently detected AresLoader, a novel loader that is found to be disseminating numerous malware families. Malware loaders are designed to deploy and execute diverse malware strains on the targeted computer system of the victim.
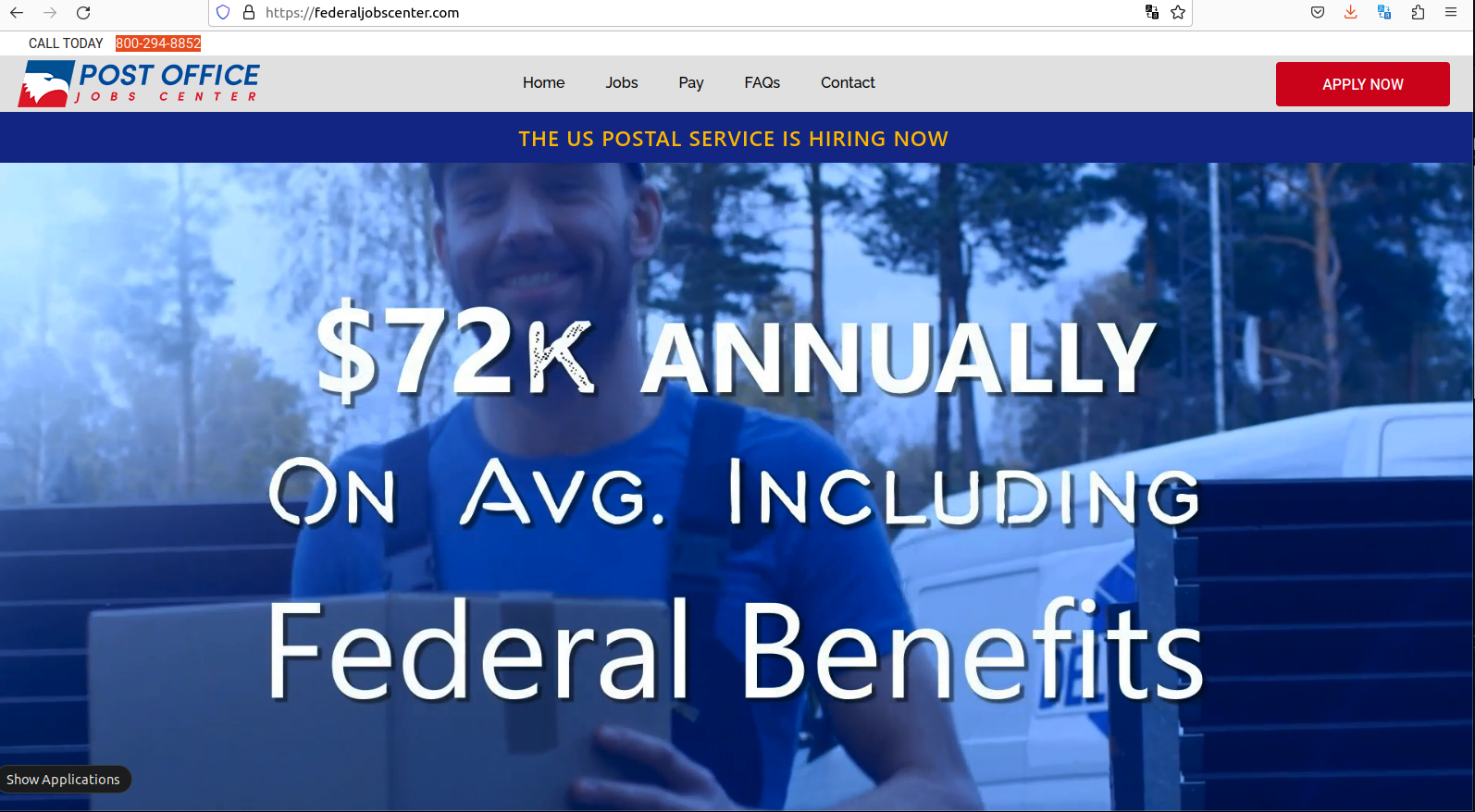
A sprawling online company based in Georgia that has made tens of millions of dollars purporting to sell access to jobs at the United States Postal Service (USPS) has exposed its internal IT operations and database of nearly 900,000 customers.
Released roughly two weeks after Google resolved two zero-day vulnerabilities in the popular browser, the latest Chrome update only resolves medium- and low-severity flaws, despite the major version change.
Despite a major push to strengthen the security of the software supply chain, a report released Tuesday from Tidelift shows more than 60% of open source maintainers describe themselves as unpaid hobbyists.
The criminal cyberattack on April 22 led Murfreesboro Medical Clinic & SurgiCenter to initiate an emergency shutdown of their network to limit the spread of stolen information within their systems.
The suspects are accused of using card skimmers and ATMs to drain electronic benefit transfer (EBT) accounts, which are used to pay for food through the Supplemental Nutrition Assistance Program (SNAP).
Researchers warn that attackers are relying more on malicious HTML files in their attacks, with malicious files now accounting for half of all HTML attachments sent via email.