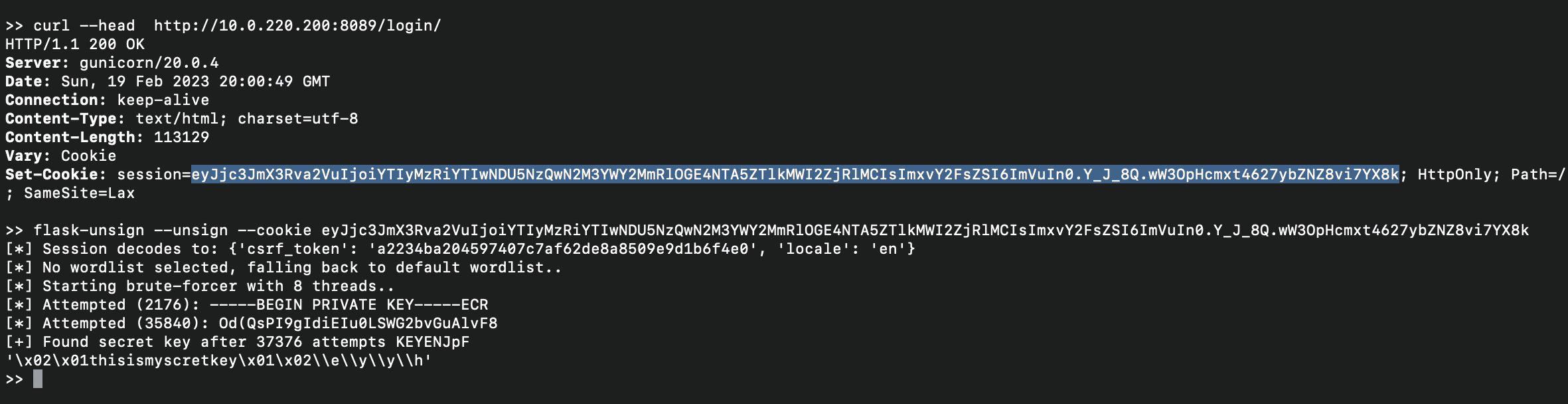
This malware is tailored to suit individual targets and exhibits a higher level of complexity, evidenced by a unique communication approach with its command-and-control (C2) infrastructure.
Cyberattackers leveraged more than 500 unique tools and tactics in 2022, according to Sophos. The data was analyzed from more than 150 Sophos Incident Response (IR) cases.
The Critical Technology Security Centers Act of 2023 introduced Tuesday by Rep. Ritchie Torres (D-N.Y.) would create two cybersecurity-focused offices to evaluate and test the security of critical technology used by the federal government.
ESET Research uncovered a campaign by the APT group known as Evasive Panda targeting an international NGO in China with malware delivered through updates of popular Chinese software.
There has been a significant number of victims in the consumer and enterprise sectors in Australia, Japan, and the U.S. after information-stealer ViperSoftX adopted new anti-detection capabilities. The enterprise sector made up over 40% of the total number of affected victims. The latest version of the info-stealer comes with the capability to steal passwords from […]
In a recent analysis, Trend Micro came across an unfamiliar program running in the background on their honeypot. It was meant to generate money by driving traffic to specific websites and engaging with ads.
Researchers found that a majority of internet-exposed instances of Apache Superset – at least 2000 (two-thirds of all servers) – are running with a dangerous default configuration. This means many of these servers are effectively open to the public.
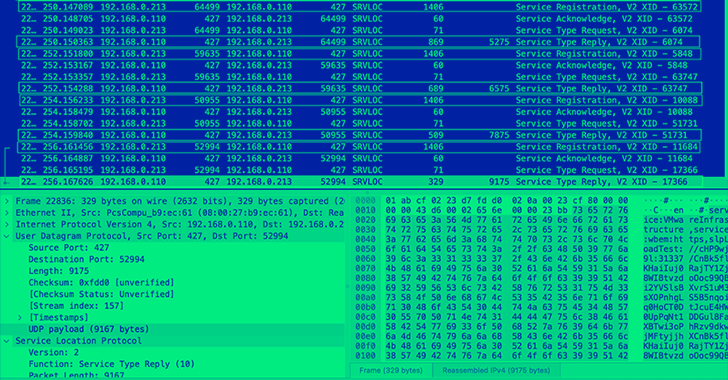
The top 10 countries with the most organizations having vulnerable SLP instances are the U.S., the U.K., Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain.
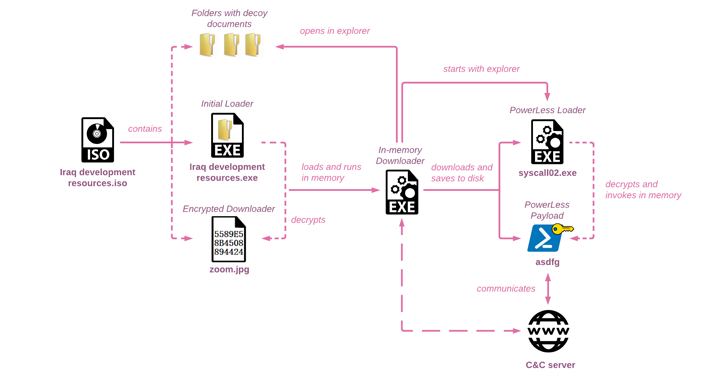
The attack chain documented by Check Point begins with an ISO disk image file that makes use of Iraq-themed lures to drop a custom in-memory downloader that ultimately launches the PowerLess implant.
Global median dwell time drops to just over two weeks, reflecting the essential role partnerships and the exchange of information play in building a more resilient cybersecurity ecosystem, according to Mandiant.